In the Q1 2019 Email Fraud & Identity Deception Trends report, we reported that the average security operations center (SOC) is getting more than 23,000 employee-reported phishing incidents per year. Those incidents would require 54 SOC analysts to handle them in a timely matter. Yet, the average SOC only has 12 security analysts.
With that kind of a gap in resources, we have two ways to address it. First, we can automate the process as much as possible with solutions like Agari Phishing Response. Second, we can pool our resources to share intelligence about email attacks to stop data breaches, which is exactly what the new Agari SOC Network™ enables.
We recently announced Agari Continuous Detection and Response, our new technology that can go back in time to find latent threats that made it past email security controls when they were first delivered. To get the most out of that technology, we need to quickly feed it new indicators of compromise (IOCs) from the Agari SOC Network.
Introducing the Agari SOC Network™
The Agari SOC Network™ is a new cyber intelligence sharing network comprised of Agari customer SOC teams, the Agari Cyber Intelligence Division, and best-of-breed machine-readable threat intelligence feeds.
As new advanced email threats are detected and confirmed by SOC teams and threat researchers, they are reported into the Agari SOC Network so those same threats can be discovered across the inboxes of all Agari customers. Then, using Agari Continuous Detection and Response, those newly-discovered threats are blocked or removed, regardless of whether they have already been delivered.
Members of the Agari SOC Network can access new threat intelligence as it appears through a mobile application that sends push notifications to mobile devices and enables analysts to review and delete malicious messages related to email security incidents around the clock.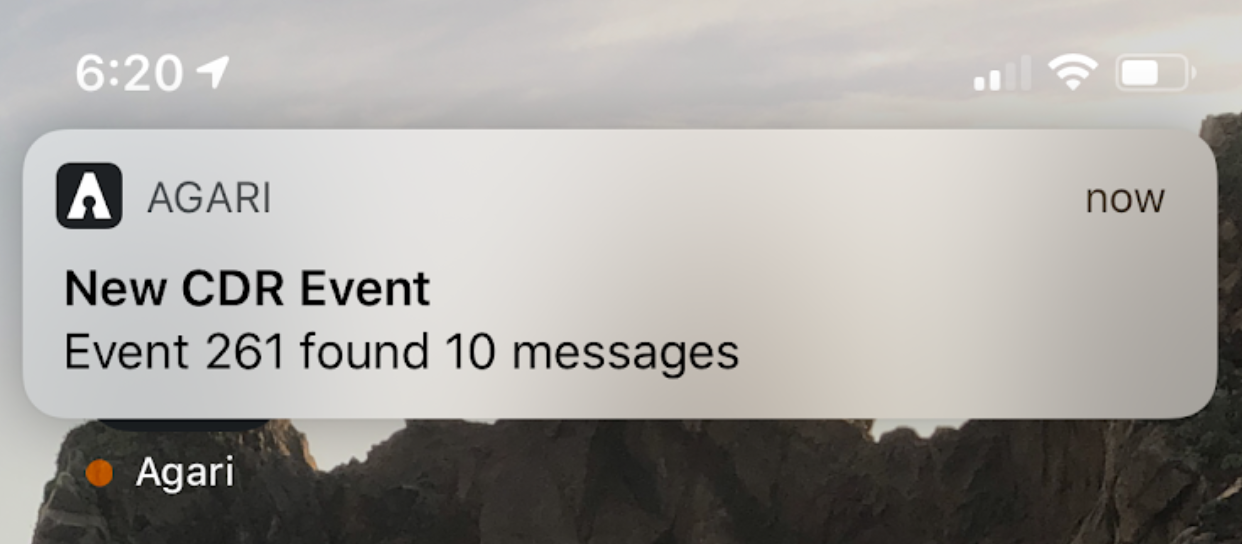
Let me give you a few examples of sources of threat intelligence that are part of the Agari SOC Network:
Agari Cyber Intelligence Division (ACID)
In December 2018, ACID published a report on a UK-based cybercriminal gang we called London Blue that has targeted more than 35,000 CFOs globally with business email compromise attacks. As of this writing, we are actively working with law enforcement to take down this group; however, in the meantime, the group continues to operate and is still targeting financial executives around the world. Now, using Agari Continuous Detection and Response, we can input new IOCs identified during our continual research into the group, such as temporary attack email accounts, subject lines, and sending infrastructure, into the network and a member of the Agari SOC Network can automatically remove all matching emails from all inboxes in their organizations. This allows Agari customers to take immediate advantage of the research our team is uncovering, without waiting for the next report to be released.
World Class Community of SOC Teams
If an Agari Phishing Response customer investigates an employee-reported spear phishing attack and determines that it is a true phish, Agari Phishing Response will post the incident with the IOCs to the Agari SOC Network so other members can immediately determine if a similar phishing attempt has hit their organization. If it has, Agari Continuous Detection and Response will automatically remove all matching emails from all inboxes in all member organizations, mitigating the possibility of a data breach. This is a powerful capability that will build on the network effect by leveraging some of the world’s top security operations centers to coordinate threat hunting and the search for common IOCs.
Best-of-Breed Threat Intel Feed
The Agari SOC Network includes many of the industry’s best threat intelligence feeds, including feeds from companies like Lastline and Crowdstrike, containing information regarding malicious URLs, malicious attachments, and sender reputation. When one of these threat intel feeds identifies new threats, it will immediately alert the Agari SOC Network so Agari customers can remove all matching emails from all inboxes in their organization.
By supplementing our own intelligence with those of our customers and threat intel feeds, we can be sure that we're discovering new phishing attempts at the moment they are sent, effectively mitigating the possibility of data breaches. The power of the Agari SOC Network lies in the sheer volume of information coming in, from the largest enterprises and best threat researchers in the world. By relying on one another to help detect and deter attacks before they can compromise employees, we can work together to ensure that humanity prevails over evil.
Starting in April, all Secure Email Cloud customers who use Cloud Email Protection and Agari Phishing Response will have access to the Agari SOC Network. From the ACID team, we look forward to supplying our unique threat intelligence related to cybercriminal gangs engaging in business email compromise to help all Agari customers leverage the power of our new continuous detection and response technology.