In December, the Agari Cyber Intelligence Division (ACID) published a report on a business email compromise group of cybercriminals we call London Blue. In this report, we documented how this group, which has roots in the United Kingdom, evolved its tactics over time, from Craigslist scams to enterprise credential phishing to business email compromise as they matured into a criminal enterprise that is structured and operates much like a modern corporation.
We also discussed how the group uses legitimate commercial services to mass harvest target data for their phishing campaigns, which included a master targeting database containing the contact information of more than 50,000 financial executives. That list was collected over a five-month span in early 2018.
Since the release of our previous report, we have continued to track London Blue’s activities in real time and now have information on how they have continued to evolve over the last few months.
London Blue Targets Agari… Again
In our last report, we mentioned that we started investigating London Blue after they targeted Agari CFO Raymond Lim in August 2018. In January, the group made the brilliant decision to try their hand at targeting our CFO for the second time. This time, we knew the malicious email was coming and we were able to observe the entire lifecycle from preparation to execution.
From initial lead collection from a commercial US-based lead service on January 11th to the time the email attack was launched on January 28th, we had full visibility into the attack process. We saw the CSV list of leads come through and watched as members of London Blue validated the data and supplemented it with open source intelligence to identify each company’s CEO, often using public company websites and LinkedIn.
We were then able to see this information as it went back to the original actor and a test email was sent in preparation for a round of BEC attacks. Once the test email was delivered successfully, the executive spoof was sent to Raymond, but was blocked by Cloud Email Protection before it hit his inbox.
Our initial engagement with London Blue during this latest campaign is shown below: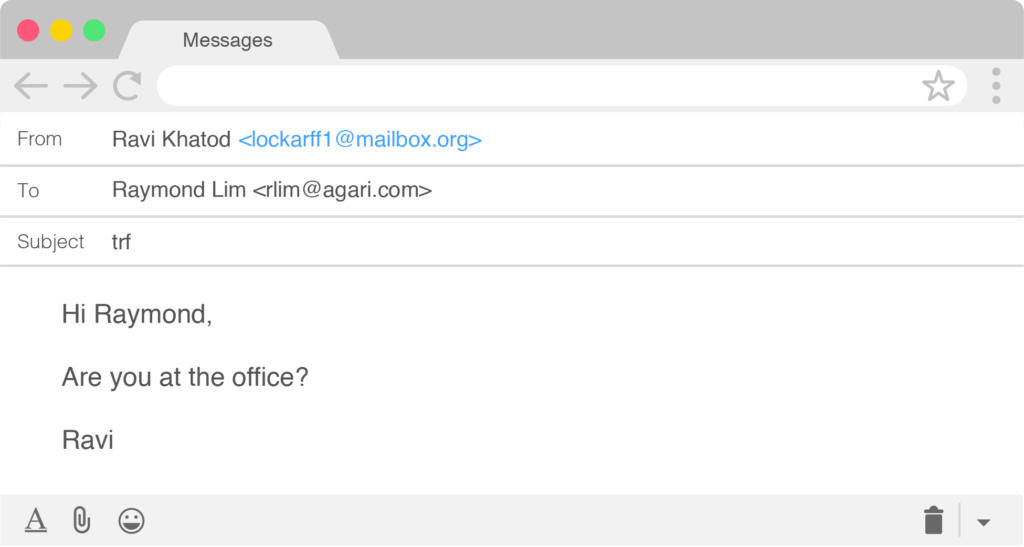

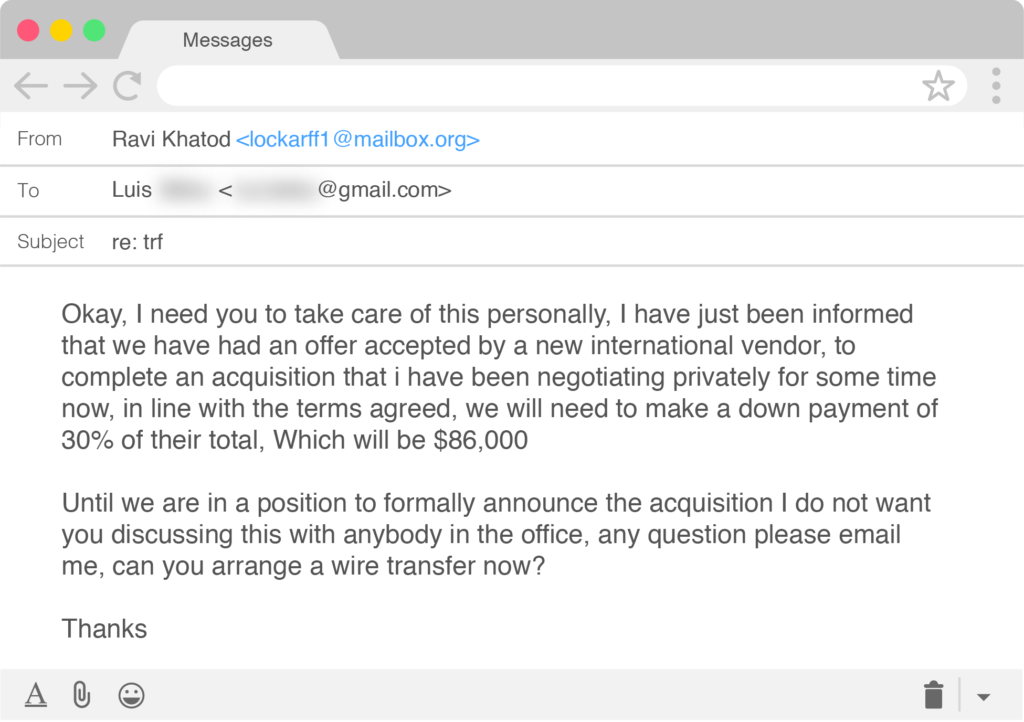
Additional emails followed, which you can view here, with London Blue actors ultimately sending account information for the wire transfer.
Gazing East into Asia and Spoofing Company Domains
During our continued monitoring of London Blue, we have observed them collect targeting information for a significant number of additional targets. Since November 2018, the group has amassed a new targeting database of nearly 8,500 financial executives from almost 7,800 different companies around the world. Similar to their previous targeting dataset, a plurality of these targets are located in the United States.
That said, one of the notable observations about London Blue’s target selection over the past five months is that many of their targets are located in Asia, an area we have not seen the group target previously. In February, London Blue collected contact information for and launched BEC campaigns against targets in Hong Kong and Singapore. In March, the group targeted employees located in Malaysia with email attacks. Interestingly, while the employees targeted by the Asia-focused attacks are located in Asia, the companies they work for are not based in those countries, but rather headquartered in the United States, Western Europe, and Australia.
Another interesting development is the fact that London Blue made a rather dramatic shift in their attack methodology starting in late-February. Rather than simply using a free and temporary email account with an imposter display name to send their BEC emails, a tactic the group has used consistently since 2016, they started spoofing the email address of the target company’s CEO as a way to add a bit more authenticity to their malicious attacks.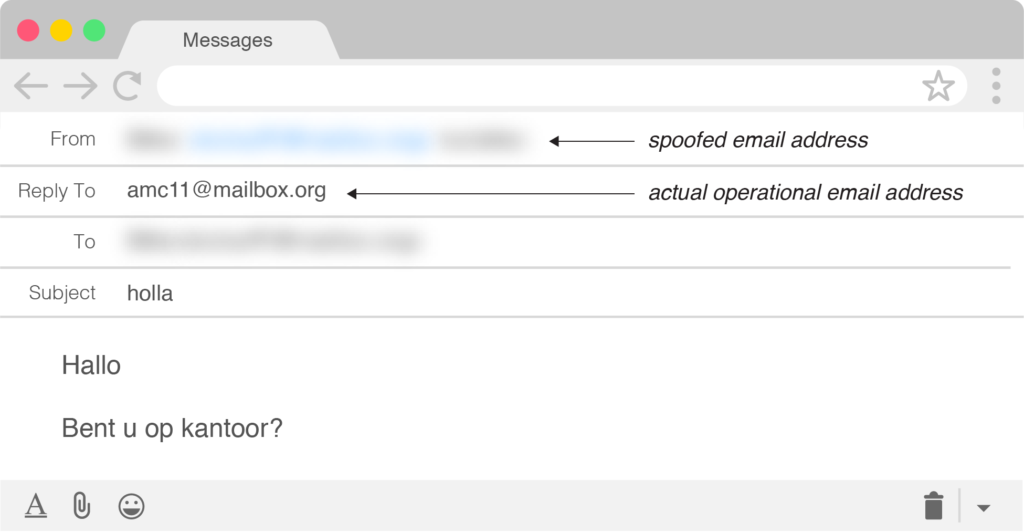
Example of a CEO spoofed London Blue email targeting a Dutch company
Unsurprisingly, most of the companies we have observed London Blue target using spoofing techniques do not have a DMARC record established. The few targeted companies that do have DMARC records set up only have their policies set to p=none, which only sends failure reports to a specified email address and does nothing to prevent a spoofed email from reaching its intended target.
Of course, Agari literally created the DMARC standard and has been helping companies protect their brands from being used for fraudulent or malicious purposes for years. #shamelessplug
For more information on the developments in London Blue, download the full report update here, which includes a full list of email addresses associated with London Blue BEC campaigns.