
On October 16 2017, the Department of Homeland Security (DHS) issued Binding Operational Directive 18-01 (BOD 18-01).
Among the measures mandated, BOD 18-01 requires that federal government agencies update their email security to adopt security standards widely used across industries: STARTTLS, SPF, DKIM and DMARC.
DMARC protects citizens and agencies from email threats. It stops cyber criminals from using phishing campaigns to exploit citizens and stops scammers from committing fraud by impersonating government agencies.
By October 2018 organizations must have a DMARC record in place and a DMARC policy set to reject. This is a very aggressive timeline, especially if a government organization has any level of complexity in their domains, email processes and technology.
If you are still working to implement DMARC and submit an Agency Plan of Action to DHS, leverage our Guide to Creating an Effective Plan of Action and our Agency Plan of Action Template.
Why Implement Email Security Protocols?
Hear from Jeanette Manfra, Department of Homeland Security, and Patrick Peterson, Founder & Executive Chairman of Agari, about the importance of BOD 18-01 and DMARC, and why Federal Agencies should implement security protocols to keep citizens safe.
Jeanette Manfra, Assistant Secretary of the Office of Cybersecurity and Communications at the Department of Homeland Security: "We have struggled within the government for years, where we have issued good policy and guidance, but it's not being taken up and adopted as quickly or as thoroughly as we wanted."
Patrick Peterson, Founder and Executive Chairman of Agari: "Organizations send email from their server...from places in the organization they didn't even know existed..and that lack of control and visibility is what makes it so easy for a cybercriminal to claim that identity."
How to meet BOD 18-01
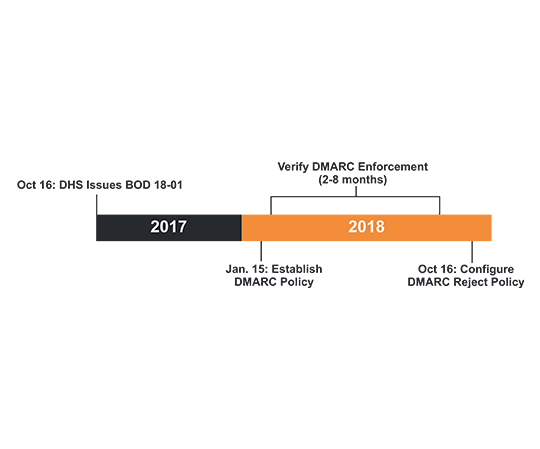
The first step – creating a DMARC record with a p=none policy – is simple; however, anything less than a quarantine or reject policy leaves the doors open to scammers.
As a founding member of the DMARC consortium, Agari understands that email ties directly to your agency’s key business processes and can be complex. Agari processes 90% of the DMARC traffic and is used by 84% of Federal domains that have a DMARC record. We know what challenges you should look out for and the critical path to move your agency to reject.
Agari email experts are here to advise and advocate for your agency. We have the technology solutions and experience to ensure that you find value and success in meeting BOD 18-01 and adopting DMARC.
The open standard called DMARC allows for email authentication to stop targeted spearfishing attacks and domain spoofing, and there are solutions out there that give you insight into what’s good and bad traffic.
Charlie Armstrong, Former CIO, U.S. Customs and Border Protection
The Solution – Agari Phishing Defense
Agari Phishing Defense is used by leading Fortune 1000 companies to proactively protect their enterprises and employees from costly BEC attacks that result in financial damage and compromised employee personal information.
Unlike other solutions that attempt to detect malicious content or use basic authentication mechanisms, Agari Phishing Defense leverages comprehensive insight into sender identities. By applying expert systems and machine learning to develop and apply trust and authenticity models, it identifies, isolates and stops email attacks that rely on identity deception.
These models are driven by the Secure Email Cloud, the only solution that verifies trusted email identities based on insight into 2 trillion emails per year.
