One of the trends that has been slowly creeping up across the BEC threat landscape is that actors are using other techniques in order to get money outside of an organization. While a traditional BEC attack includes instructions for wiring money outside of the organization, more and more actors are asking for a large number of gift cards instead of the classical request of “Please wire $30,000 to beneficiary.” So if an organization is victimized and is tricked into sending gift cards to a scammer, how does the actor monetize them and how much money do they actually make?
Gift Cards Emerging in the BEC Threat Landscape
The use of gift cards as a cash out method has been a burgeoning trend in the BEC threat landscape over the past year. Data from the Federal Trade Commission (FTC) indicates that in 2015, just seven percent of scam victims reported losing money via gift cards. By the end of 2018, though, more than a quarter of all scams used gift cards as a cash out mechanism.
Similar data was observed by the Internet Crime Complaint Center (IC3). An October 2018 report from IC3 shows that the frequency of BEC gift card scams was minimal until the first quarter of 2018, when the prevalence of these attacks skyrocketed and continued to rise throughout the year.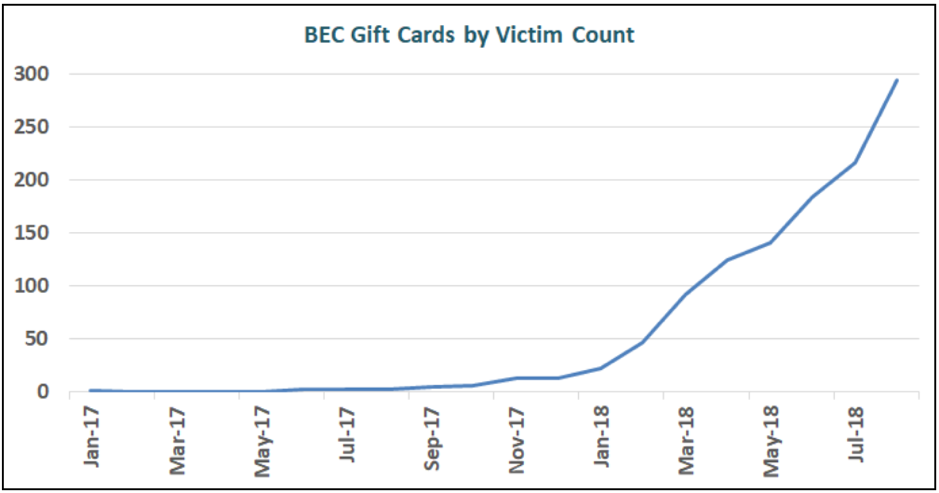 Trend of Gift Card BEC Attacks (Source: IC3)
Trend of Gift Card BEC Attacks (Source: IC3)
Interestingly, we’ve also seen instances where gift cards and wire transfers are requested by BEC actors within the same scam. Frequently, we see that once a BEC target has been victimized, a scammer comes back again with subsequent attacks. In the example below, which occurred during one of our active defense engagements, after thinking that a requested wire transfer is pending, the scammer immediately asks our persona to purchase Apple iTunes gift cards for client gifts.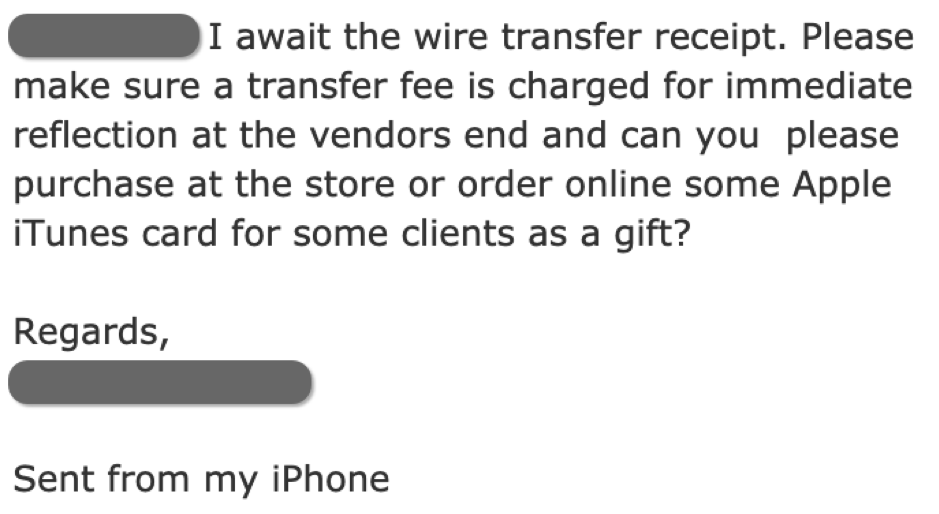
Why Gift Cards are Becoming a Preferred Cash Out Instrument
Using wire transfers has netted BEC scammers more than $12 billion since 2013 and gains from BEC attacks have continued to grow annually at an astounding rate, so why would they change their methods now?
First, successful collaboration between industry researchers, financial institutions, and law enforcement has made the identification and mitigation of suspected mule accounts more impactful, shortening the effective lifespan of these accounts. Using gift cards, cyber threat actors are able to receive illicit funds in a way that does not come into contact with accounts that could get shut down.
Second, by using gift cards, cybercriminals eliminate the need for a middleman to receive and redirect stolen money. Money mules are individuals that are generally located in the same country as a victim company and help a scammer launder stolen proceeds through their bank account. For their part in the scheme, money mules typically keep a percentage of the stolen funds. Using gift cards, a BEC actor is able to bypass this process and receive the stolen funds directly.
One of the biggest downsides of using gift cards as a cash out mechanism, though, is that the financial gain for an individual attack is typically significantly less than a successful wire transfer. As documented in “Behind the ‘From’ Lines,” the average amount requested in BEC attacks using fraudulent wire transfers is $35,000. The average amount gained through a successful gift card BEC scam, on the other hand, is generally between $1,000 and $2,000.
Laundering Dirty Gift Cards
Of course, gift cards are not what BEC scammers are actually after. They’re looking to pad their bank accounts with cash. So how to scammers convert the gift cards they collect from victims into cash?
In our recent report on a group we call Scarlet Widow, we summarized our direct visibility into the group’s methods of laundering illicit gift cards through multiple online services into NIgerian bank accounts. The methods used by Scarlet Widow are identical to those used by a number of other West African cybercriminal groups we have tracked.
The primary service used by BEC threat groups to monetize gift cards is Paxful. Paxful is a US-based peer-to-peer marketplace that allows users to buy bitcoin from other users using hundreds of different payment methods, including dozens of different types of gift cards. The most common gift cards traded on Paxful are Apple iTunes, Amazon, Google Play, and Steam Wallet. Incidentally, these are also the most common gift cards requested by scammers in gift card BEC attacks we’ve observed.
To trade gift cards on Paxful, though, sellers take a significant hit when it comes to exchange rate. For example, most Apple iTunes gift cards are traded at 40 to 80 cents on the dollar.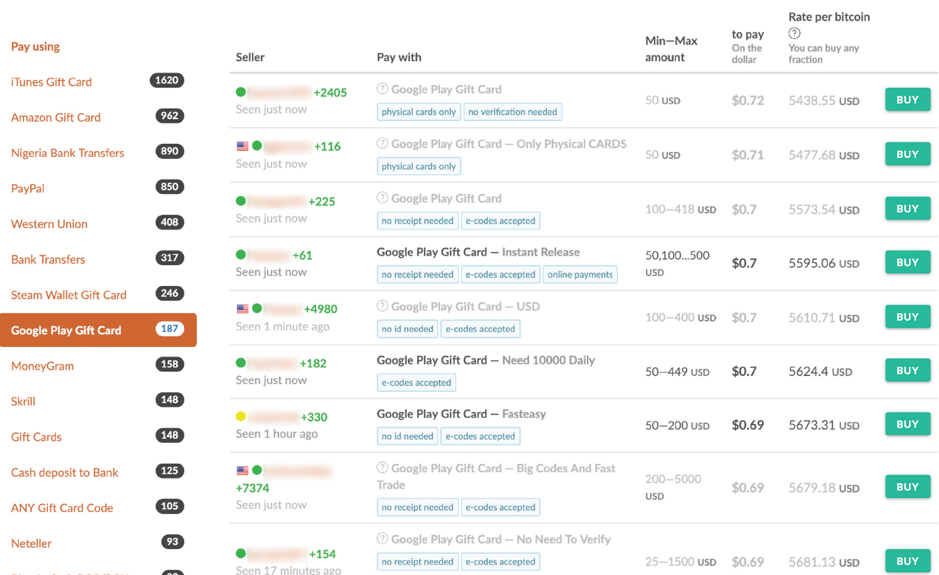
Example of Google Play gift cards posted for trade on Paxful
After a gift card has been traded for bitcoin, the funds are deposited into a wallet, but the cryptocurrency still needs to be converted into cash. To do this, Scarlet Widow moves bitcoin from their Paxful wallet to a wallet on another peer-to-peer cryptocurrency exchange: Remitano. On Remitano, users are able to advertise their bitcoin for sale and a buyer can purchase the Bitcoin for a specified price via bank transfer.
Once a scammer has exchanged their bitcoin and the buyer’s funds are in their bank account, the process of converting illicit gift cards into cash is complete.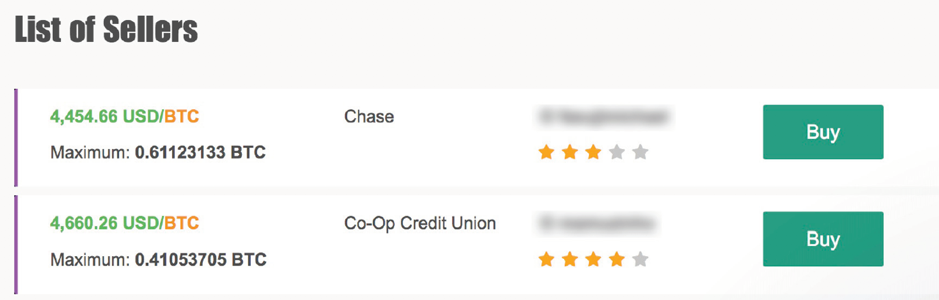
Example of Bitcoin being offered for trade on Remitano
The volume of transactions for some of the BEC actors we’ve tracked is significant and is a good indicator of the success rate of these types of attacks. One cybercriminal we are tracking successfully traded 140 iTunes gift cards obtained from successful BEC attacks on Paxful during a six month period in 2018.
The entire laundering process for illicit gift cards is surprisingly fast. In August 2018, thinking she had received a request from the head of the university’s Finance Department, Scarlet Widow tricked an administrator at an Australian university was tricked by Scarlet Widow into buying $1,800 in Apple iTunes gift cards and sending pictures of the redemption codes to Scarlet Widow. From the moment the victim sent the first gift card to the group, they were immediately posted for trade on Paxful and the entire laundering process occurred in parallel as the victim continued to send pictures of additional cards. By the time the cards had been laundered, the group had converted the gift cards into $700 in cash and the entire process, from receipt of the first gift card to transferring cash into a bank account, took less than two-and-a-half hours.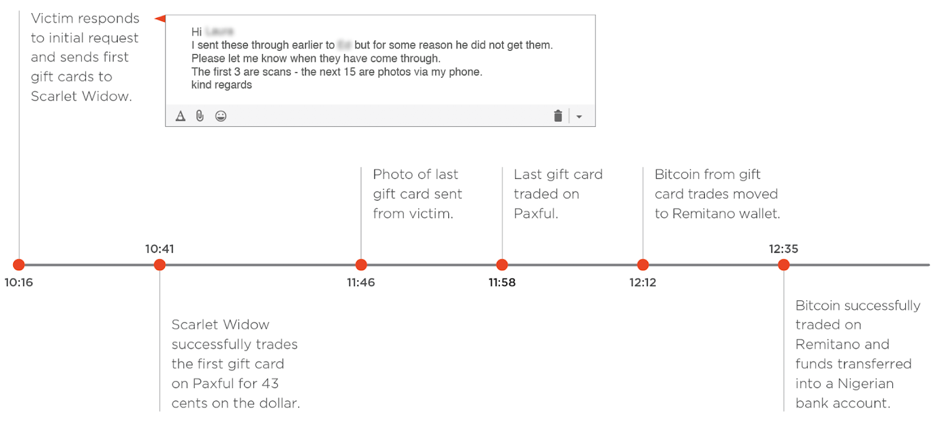
Timeline of Scarlet Widow gift card laundering process
At the end of the day, if you get a request from your CEO to buy gift cards for a client or employees, confirm the request with them in person first before making the purchase. One of the best ways to prevent BEC attacks within your organization is to set up a formal internal process for handling requests for financial transactions so if a request diverges from this process, red flags will be raised. And chances are that if a gift card request is legitimate, the CEO won’t ask you to scratch the card off and send them a picture via email.
