California has witnessed its most deadly and destructive wildfire on record during the month of November. As the Camp Fire blazes on, more than 70 people have died, hundreds are still missing, and in some cases, entire towns have been reduced to little more than ashes. What’s more is that impending rain threatens to bring mudslides and further destruction to an already ravaged area.
Despite the devastating effects tragedies such as this have, it is always to some extent countered by acts of extreme bravery and heroism, as communities and emergency services galvanize to face the natural disaster that is still unfolding. Tragic incidents may reveal the best in humanity—oftentimes resulting in heroic displays of strength and compassion. But for a small group of people, they are the trigger for quite the opposite. For these people, tragedy allows—and even encourages—greed, opportunism, and deceit to come to the fore.
Cybercriminals Taking Advantage of Tragedy
Agari has recently seen evidence that cybercriminals are adapting successful email scam techniques to include references to the California wildfires, both in Northern and Southern California. Particularly within workplaces, gift cards are being solicited from unsuspecting employees so that they can be sent to supposed clients as financial assistance to help them during the disaster. In these cases, the criminal actors are adopting the identity of the targeted organization’s CEO and sending emails to employees who work in accounting, finance, or administration.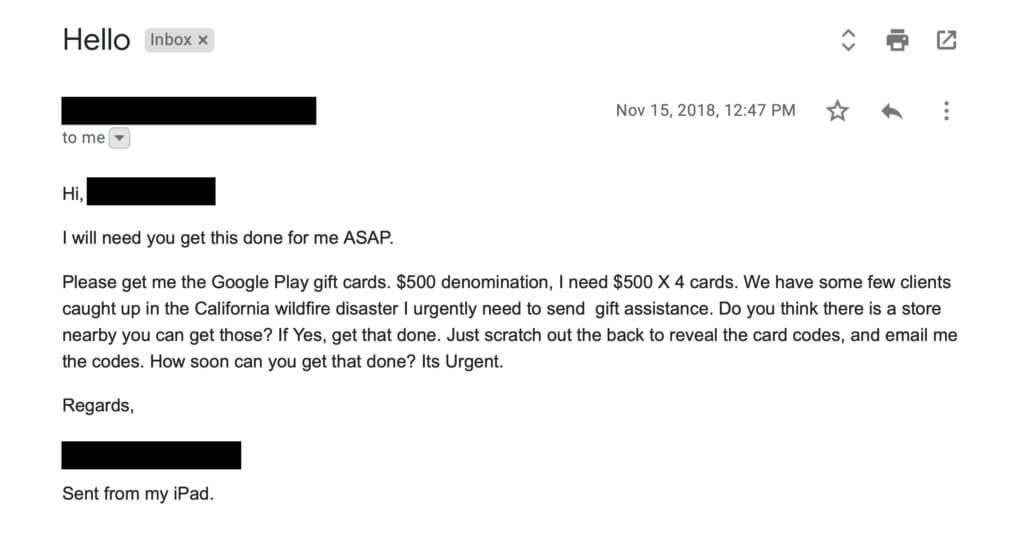
The first email sent by the fraudulent CEO makes a general inquiry regarding the employee's availability to carry out a task for them. This is then followed up with a reply similar to that shown above. If the scam is successful and the employee purchases the gift cards, they will be asked to scratch off the reverse, and send scans or photos of the cards to the executive (aka the criminal) via email. Once the criminal is in receipt of the codes, which are practically untraceable, they can then exchange them for currency from any location in the world using a multitude of online services.
Removing Cybercriminals from the Equation
Relevance and topicality are two of the main tools cybercriminals will leverage to obtain money or information through email deception. It was only back in September this year that the US Government issued warnings about phishing campaigns targeting those affected by Hurricane Florence, but the reach of these warnings can be hard to ascertain, especially under such pressurized circumstances.
That’s not to say that there are not legitimate organizations who are helping the victims of these wildfires. Hundreds of organizations have already come forward to help victims impacted by the Camp Fire in California. There is always good in the world, and the presence of those willing to help should not be discounted.
However, should you receive an email such as the one shown above, remember to validate the request using a channel other than email—such as a text or a call. This quick verification can save the organization thousands should the request not prove to be legitimate. And as a more general guide to handling requests for donations, look to make contact with a reputable and established charity. The true victims of tragedies—not those playing off their misfortune—will thank you.
To learn more about how cybercriminals impersonate CEOs and other executives for personal gain, download a copy of "Behind the 'From' Lines: Email Fraud on a Global Scale."
Hostile Landscape of Email Threats Leverages California Wildfire Tragedy
Posted on November 20, 2018