There is no denying that business email compromise (BEC) is big business, with losses exceeding a billion dollars in the United States in the last year alone. Globally, BEC attacks have cost more than $13 billion in the last five years. Chances are likely that you’ve probably been a recipient of one of these social-engineered emails yourself. But the question remains… who is behind these increasingly sophisticated email attacks, and why did they become so popular in recent years?
Introducing Scattered Canary
In a first, the Agari Cyber Intelligence Division (ACID) has cataloged the evolution of a Nigerian cybercriminal organization from its emergence as a one-man shop into a powerful BEC enterprise employing dozens of threat actors. With this West African gang we’ve named Scattered Canary, we have deep insight into how the group grew from a single cybercriminal working Craigslist scams into an entire organization that consists of dozens of criminals, each with specific tasks.
When the first member of Scattered Canary, who, for the purposes of this report, we call Alpha, began his operations, he was a lone wolf—working mostly Craigslist scams as he learned the tricks of the trade from a mentor. However, within a few years, he had honed his craft enough to expand into romance scams, where he met his first “employee,” Beta. Once they had secured enough mules via their romance scams to launder their stolen money, they shifted from targeting individuals to targeting enterprises, and the group’s BEC operation was born.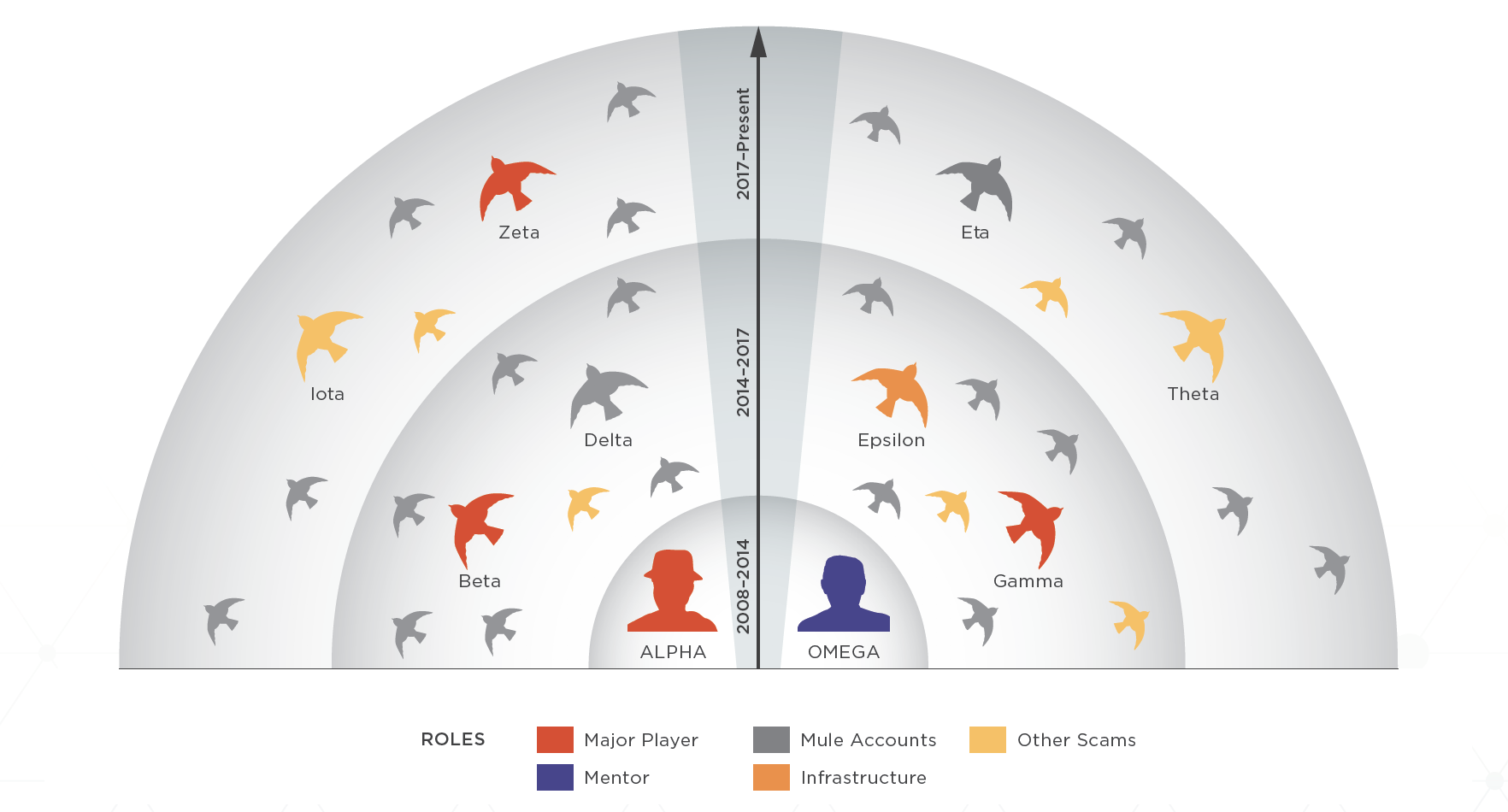
Since its inception, at least 35 different actors have joined Scattered Canary in its fraudulent schemes. The group has turned to a scalable model through which they can run multiple types of scams concurrently. And with multiple tools designed to help them expand their operations and stay hidden from law enforcement, it is no wonder that they are seeing massive success.
Go Big or Go Home
While BEC remains a favorite due to its ease and success, a look into Scattered Canary’s operations demonstrates that these groups are not one-trick ponies. At any given time, Scattered Canary is involved in a number of different types of scams simultaneously—including romance scams, tax fraud, social security fraud, employment scams, and more. And this is only one organization, out of the many currently residing in West Africa and around the world.
With this much involvement between members, and so much connection between crime type, we must look at the bigger picture to truly understand the enormity of the cybercrime problem.
If Scattered Canary can be seen as a microcosm for the rapidly evolving organizations behind today’s most pernicious email scams, our new report demonstrates that a much more holistic approach—one based on threat actor identity rather than type of fraudulent activity—is required to detect email fraud and protect organizations.


