You likely have a fraudulent email from a business email compromise (BEC) scammer sitting in your inbox, and you may not realize it. However, recent research from the Agari Cyber Intelligence Division (ACID) has shown that these advanced phishing attacks increasingly possess a handful of commonalities, making them easier to spot—which is good news considering their popularity.
There are more BEC scams now than ever before, and they're growing increasingly effective. The FBI reports there were more than 351,000 email scam complaints last year, while losses from those designed to fool recipients into transferring wire payments for fraudulent invoices nearly doubled year-on-year, to nearly $1.3 billion.
These attacks continue to grow more sophisticated in the way they impersonate trusted brands and individuals in order to manipulate their targets into acting before thinking to verify the legitimacy of the request. Our researchers identified a few key characteristics common to a growing number of BEC emails over the last three months, which we’ve published in our latest report on trends in email security.
They're Short—and Consistent
In most cases, the initial email in a BEC attack is very brief, comprised of just a few words or sentences designed to push emotional buttons. Maybe it's a last-minute request from a senior executive, a pointed payment "reminder" from a key supplier, or an "account alert" from the bank or a technology vendor, but regardless of the ploy, these emails designed to prompt an immediate response.
The email subject lines themselves are frequently very generic, so as not to arouse suspicion. That said, they almost always contain specific keywords meant to generate urgency. In fact, one in four BEC emails observed during the first quarter of this year contained one of three words in the subject line: "Quick," "Request," or "Urgent."
They're Personalized and Persuasive
Today, 20 percent of BEC scams are personalized to include the name of the recipient to help convey legitimacy. As you can see above, that includes four of the top 10 BEC subject lines. Though subtle, it's easy to see how this extra step can contribute to a malign message's verisimilitude.
After all, the email address appears to check out. Sixty-seven percent of these emails leverage display name deception using Roadrunner, AOL, Gmail or another (typically free) webmail account. Another 28 percent use look-alike domains to pull off the guise. While there is usually a cost associated with registering a domain, the ability to create a more authentic-looking email address is worth the price for some. Additionally, a small but troubling five percent come from email accounts that have been compromised.
Combined with the correct name of the recipient, and a message that makes sense given the context and the relationship with the perceived sender, these malicious emails lower the recipient's defenses and lessen the likelihood they'll recognize the scam.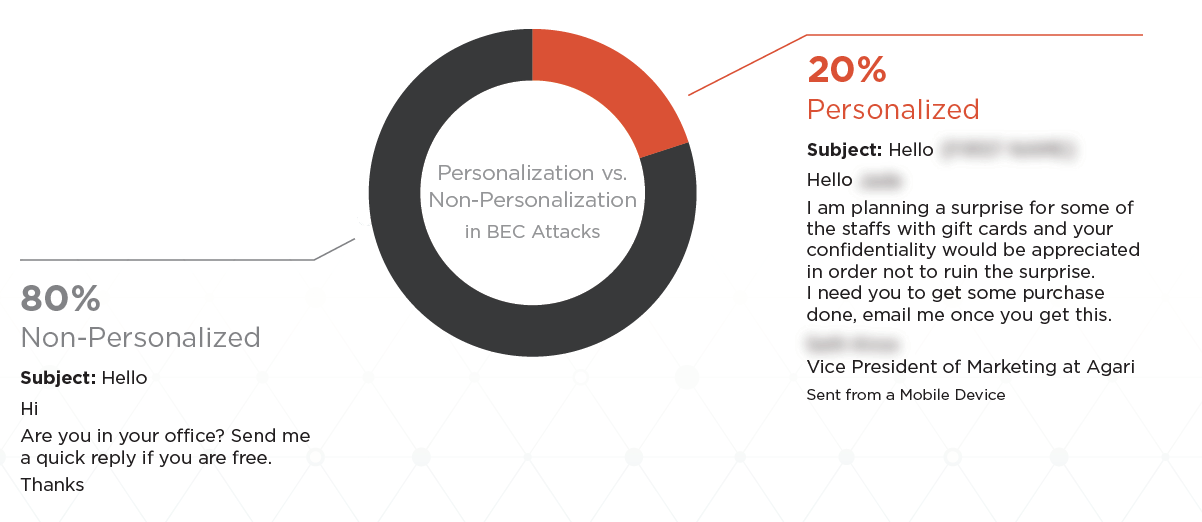
They're Sent by Professionals
Personalization also demonstrates the level of reconnaissance some cybercriminal organizations are able to conduct prior to launching BEC campaigns. Instead of simply scraping email addresses from company websites, some BEC groups curate target lists of specific executives—typically in finance—for use in crafting these personalized messages.
Our previous research has shown that many BEC groups even use legitimate commercial lead generation services to construct tailored queries and collect comprehensive contact information on financial executives around the world. All of this work means their attacks are becoming as wholly believable as they are effective.
They’re Going Unchecked
As average losses from successful BEC attacks continue to grow, the way organizations respond to this growing threat is of critical importance. Yet today, it's unclear how many organizations are deploying the modern defenses needed to fight back against BEC emails that easily bypass SEGs and other security controls. The Agari Identity Graph™, for instance, leverages data science and real-time intelligence from trillions of emails to establish normative, trusted behaviors and signals between email sender and recipient—including devices, message volumes, locations, and more—to spot and neutralize advanced email threats other controls can't catch.
Until organizations decide to take steps to protect themselves, BEC emails sharing many key traits will continue bypassing other security controls on their way to employee inboxes. And the eye-popping revenues perpetrators generate with so little effort or overhead will continue to add plenty of insult to the injury.
To learn more about emerging trends in BEC and other advanced email threats, download the Email Fraud and Identity Deception Report.