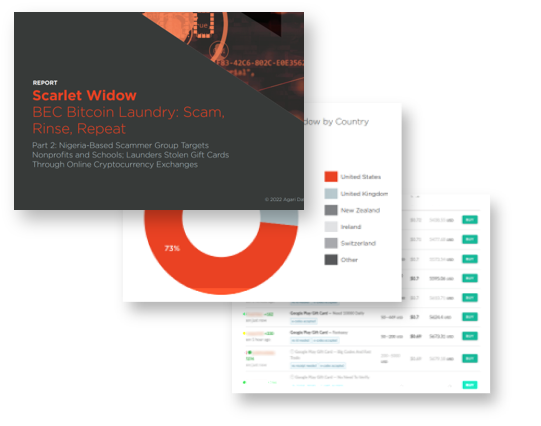
While many cybercriminal gangs scam medium-sized and large corporations, Agari has now uncovered and documented the practices of a Nigeria-based scammer group, dubbed Scarlet Widow, that has evolved a different strategy focused on more vulnerable sectors such as school districts, universities, and nonprofits.
Image
In this report, we uncover:
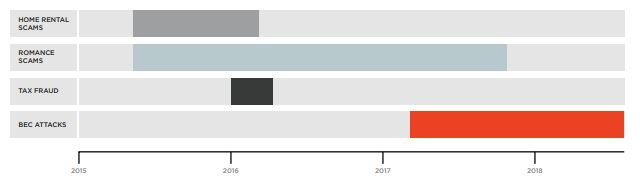
- How Scarlet Widow transitioned from romance scams to tax fraud to BEC
- Why the group focuses on school districts, universities, and nonprofits
- What kinds of emails Scarlet Widow uses to target their victims, and
- How the cybercriminals launder the money through legitimate online services
Download Scarlet Widow: BEC Bitcoin Laundry—Scam, Rinse, Repeat to see why cybercriminals are going after more vulnerable populations in their scams.