Why Integrated Email Threat Data Matters
Email is a primary vector for attacks on your business today—and email threats are evolving faster than ever. But actionable data about email attacks is often inaccessible to time-strapped security operations and incident response teams. That disconnect leaves your business vulnerable and unable to mitigate hidden email threats.
Improve Visibility with Integrated Email Threat Data
The Agari App for Splunk solves this challenge and makes it easy to surface email threats by quickly integrating valuable Agari threat intelligence into your Splunk dashboard. Your team can analyze and correlate Agari data, query logs to trigger custom alerts, and create shared views and dashboards for stakeholders in your organization.
Accelerate Incident Response and Drive SOC Efficiency
The Agari integration with Splunk empowers security teams to work more effectively to mitigate email threats. Leveraging Agari incident data and Splunk tools, security analysts can incorporate email incidents to improve investigations and accelerate resolution—without needing to jump through hoops to transform log data or manually import feeds. With the ability to track and resolve security incidents through a single pane of glass, your team can focus on remediation of email threats, not repetitive labor and administrative overhead.
Leverage Your Strategic Splunk and Agari Investments for Security
Agari threat data integration with Splunk Enterprise and Splunk Cloud ensures email incidents can be managed in Splunk’s on-premises and cloud-native SIEM environments alike. The Agari App for Splunk supports key Agari products that protect your inbound and outbound email streams, including Agari DMARC Protection and Cloud Email Protection. Integrating email threat data across applications helps you get maximum value from your security investments and helps to safeguard your entire infrastructure against email threats.
Operationalize Email Threat Data to Quickly Deliver Results
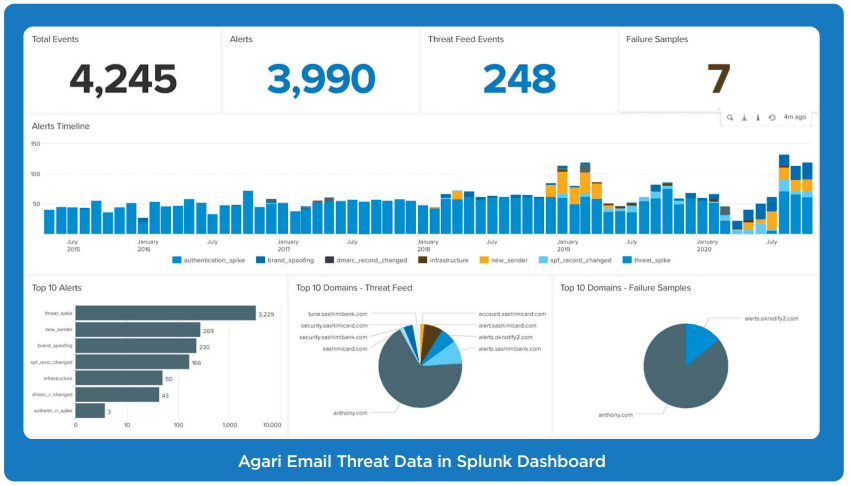
The Agari App for Splunk helps your team quickly operationalize email threat data to realize value for your organization by surfacing email threats; creating standard security and compliance workflows; and simplifying incident tracking and case management.
The integration reduces complexity and includes more than ten preconfigured dashboards that enable quick visual inspection and identify policy hits including:
- Top attack types
- Top users attacked
- Threat feed spike alerts
- Authentication spikes
- Brand spoofing alerts
- DMARC record alerts
- Failure samples and more
- RUF data for monitoring for email domain abuse
Get Started Today
The Agari App for Splunk is available to install from the Splunkbase directory today. Contact your Agari representative to learn more.