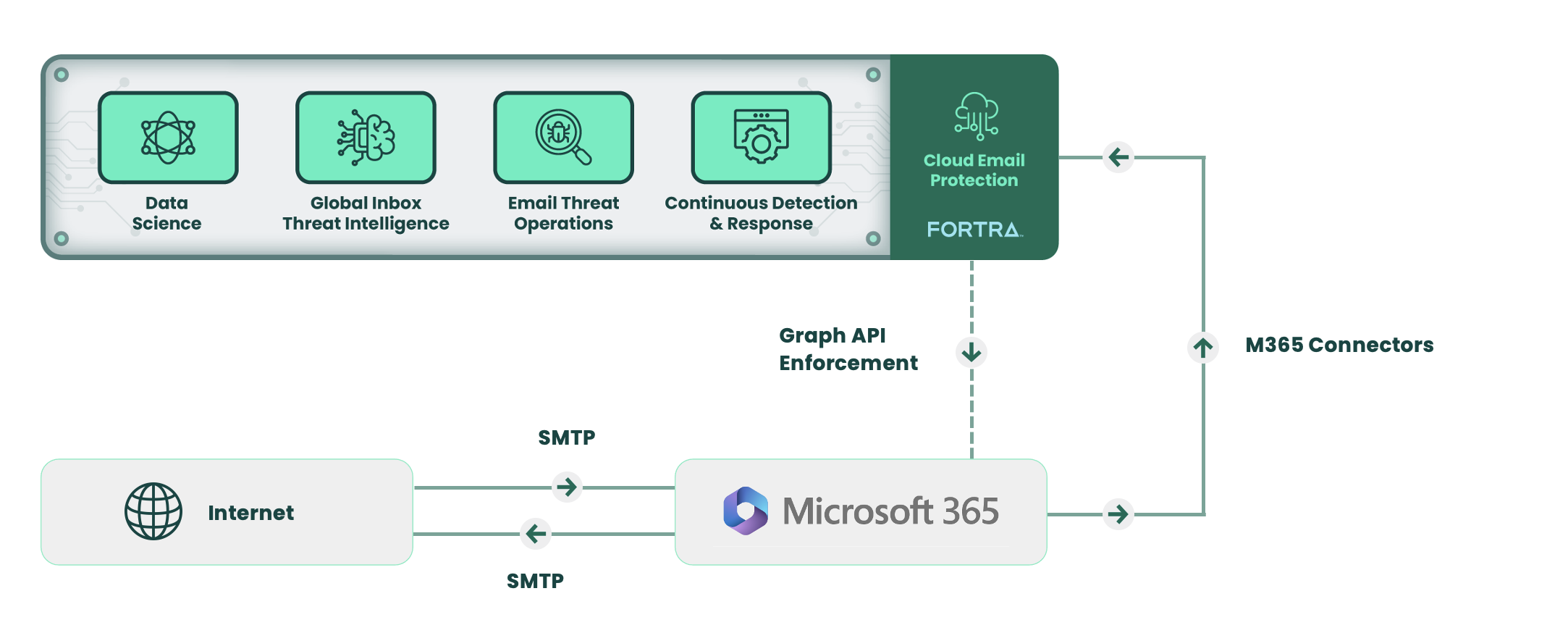
Advanced email threats use impersonation and other techniques to easily bypass traditional email defenses like Secure Email Gateways. And while there are bolt-on security upgrades offered by cloud email providers–like Microsoft 365–they offer little protection against sophisticated threats. Once these malicious emails make it into user inboxes, cleaning them up is costly and arduous.
Fortra's Cloud Email Protection is an integrated cloud email security (ICES) platform that detects and automatically remediates advanced email threats. With Fortra's Cloud Email Protection, enterprises can simplify and scale their email security to stop BEC, spear phishing, and targeted social engineering.
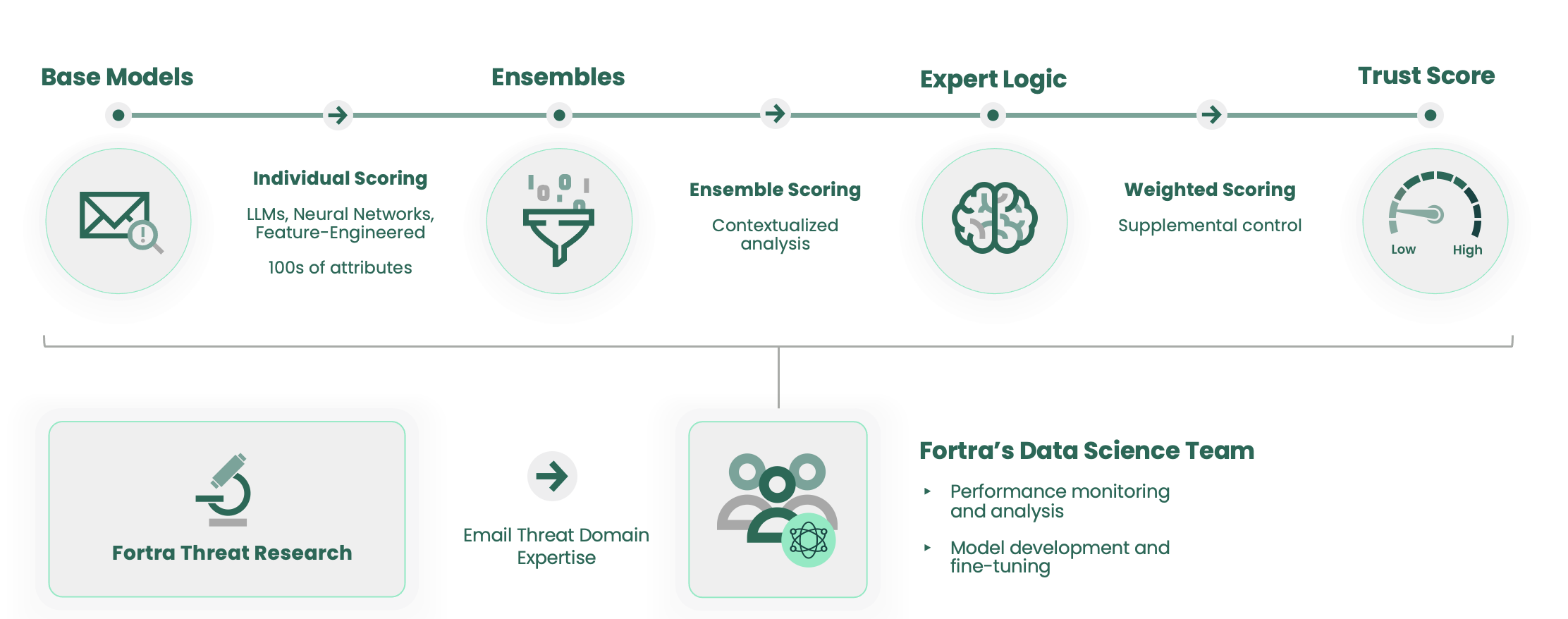
Detect Deception with Data Science Models
Fortra's Cloud Email Protection uses a combination of machine learning,
large language models (LLMs), and neural networks to evaluate hundreds of message attributes in real-time. Fortra’s dedicated team of data scientists take advantage of our unique visibility into email threats that reach user inboxes to develop and train models. As a result, Fortra's Cloud Email Protection can detect truly unknown threats that would go unnoticed by signature or pattern-based defenses and fool even the most sophisticated end users.
Leverage Internal Intel and Global Threat Indicators from Inboxes Worldwide
Fortra's Cloud Email Protection is continuously enriched by threat intel that’s been curated from user inboxes globally. When a new email threat is observed bypassing the on-prem Secure Email Gateway or other traditional security defense for any of our customers, Fortra’s experts analyze it and extract threat indicators such as O365 lures, malicious senders, files, domains, and URLs. Simply, Fortra's Cloud Email Protection automatically applies these indicators to find and remove emerging threats across all customers.
Proactively Hunt for Novel Email Attacks
Fortra’s Email Hunting Operations is a dedicated team of analysts that dig deeply into threat data across our customers to proactively identify novel attack patterns and implement countermeasures in Fortra's Cloud Email Protection. These experts use advanced data mining techniques to spot and investigate suspicious activity across massive volumes of email threat data. When a new attack pattern is uncovered, they immediately develop tactical countermeasures to detect and stop the threat across our customer base.
Continuously Eradicate Threats Across Inboxes
Fortra's Cloud Email Protection includes an integrated logic-based policy enforcement engine called Continuous Detection and Response (CDR). Designed for enterprise scale, CDR automates key email security processes, such as finding and purging threats throughout the email environment. Data Science Trust Scores, Global Inbox Threat Intel, BEC Intel, and email threat policies are all enforced “out-of-the-box” by CDR. Additionally, customers can use CDR to configure their own policies specific to their native emailenvironments.
Complementary Fortra Cybersecurity Solutions
Fortra’s Cloud Email Protection pairs well with the following Fortra Email Security solutions:
- Suspicious Email Analysis provides expert triage and automated response to user-reported emails
- DMARC Protection automates and simplifies DMARC email authentication and SPF and DKIM protocols
- Domain Monitoring service streamlines mitigation through registrar partners and escalation procedures
- Security Awareness Training provides interactive courses to help employees identify cyber threats
- Threat Intelligence Services equip SOC teams with insights that aid in threat disruption and enrich controls