A 25% spike in employee-reported phishing attacks during the first quarter of 2019 has increased the time required for security operations centers (SOCs) to respond to phishing incidents by as much as 32%—and the price tag is rising fast.
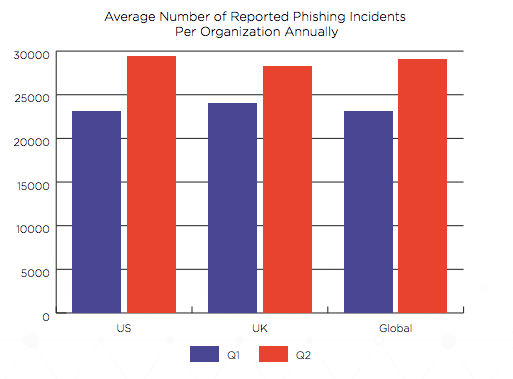
According to the new Q2 2019 Email Fraud and Identity Deception Report from the Agari Cyber Intelligence Division (ACID), employees now report an average of 29,028 phishing incidents to corporate SOCs per year—a 25% increase in just ninety days. Meanwhile, the average time it takes to triage, investigate, and remediate these incidents jumped to 6.5 hours, up from 4.9 hours during the previous quarter.

In all, the projected cost to SOCs nearly doubled during the same period, exceeding an average $8.1 million on an annualized basis. For US-based companies, this matters—a lot. Today, a successful phishing attack can lead to losses of as much as $1.6 million. If it results in a data breach, costs skyrocket to an average of $7.9 million per incident.
According to Ponemon Institute, the probability of falling victim to a breach is now 14% per year. And it's getting worse—in part because of the very mechanisms businesses are putting place to mitigate the issue.
The fact is, even with today's most advanced threat protection solutions in place and the best security awareness training available, there is no possible way to completely remove the risk that an employee will fall for a phishing email designed to defraud the company or steal sensitive information as part of a data breach.
As part of our quarterly reports, ACID surveys SOC professionals at 280 large organizations to get a read on the state of incident response in a rapidly evolving threat landscape. In addition to security awareness training and phishing simulations, this quarter's survey finds that 95% of businesses have implemented solutions that give employees the ability to report suspected phishing emails. But all too often, employee-reported emails end up flooding SOCs with more incidents to triage, investigate, and remediate than they can handle.
What's more, nearly 56% of all those reported incidents are false positives. That's up 7% in the US, and 10% globally, in just three months. Combine it with the increased volume of employee-reported incidents overall, and a number of significant challenges become immediately apparent.
As just one example, the new 2019 Verizon Data Breach Investigations Report finds that in 40% of all breaches, data exfiltration begins within minutes. Unfortunately for everyone involved, it takes most companies months or even years to discover them and even longer to repair the damage. With employee-reported phishing attacks rising rapidly, the distance from breach to remediation is likely to grow worse.
In the face of all of this, the number of SOC analysts per organization hit 14.5 in Q1. The good news is that is a 16% increase from the previous quarter.
Specific numbers can vary widely based on the size of the organization or the total volume of phishing attacks. Approximately 41% of organizations with more than 10,000 employees have 20 or more SOC analysts. The same applies to those hit with 60,000 or more phishing incidents annually, no matter the size of the company. Yet while rising analyst headcounts are encouraging, a persistent SOC staffing gap continues to grow more precarious.
Based on the average number of incident reports and the amount of time it takes to remediate them, SOCs would need 90 analysts to handle the number of reported phishing incidents they receive each year. That represents $8.1 million in annual staffing costs—up 200% in just three months.
On average, that means SOCs need to hire 76 full-time equivalents to avoid the heightened risk of data breach and fraud. But for many, there is a far easier solution.
According to this quarter's survey results, SOC professionals estimate that they could reduce their company's breach risk an average of 51% by automating phishing incident response processes. In fact, that could have a cascading effect that could dramatically lower SOC costs overall.
To solve this exact problem, Agari Phishing Response is a one-touch automation solution that has been shown to reduce the time needed to triage, investigate, and remediate phishing incidents by as much as 90% in real-world implementations. As a result, security teams can ignore false positives and focus on real attacks. Furthermore, breaches can be identified and contained in mere minutes instead of months, helping SOCs save time while helping their organizations avoid millions in potential losses.
Applying the SOC analyst's estimated reductions across the data captured in the Q2 report, it's possible to estimate that a solution such as Agari Phishing Response could help organizations realize $7.29 million in SOC analyst time savings relative to estimated staffing requirements. They can also pocket another $561,025 in savings from that 51% reduction in breach risk. The grand total: an average $7.85 million in annual savings.
There have already been more than 281 significant data breaches so far this year, and they aren't slowing down. Yet despite all the risks, nearly 20% of IT and security leaders say their organizations are more vulnerable to data breaches than they were in the preceding 12 months. Indeed, the targeted phishing attacks that can lead to such breaches rank as the #1 cybersecurity threat organizations face today. Which means finding new ways to automate and accelerate phishing incident response times is more important than ever.
To learn more about trends in phishing incident response, download a copy of the Q2 2019 Email Fraud and Identity Deception Report.
According to the new Q2 2019 Email Fraud and Identity Deception Report from the Agari Cyber Intelligence Division (ACID), employees now report an average of 29,028 phishing incidents to corporate SOCs per year—a 25% increase in just ninety days. Meanwhile, the average time it takes to triage, investigate, and remediate these incidents jumped to 6.5 hours, up from 4.9 hours during the previous quarter.

In all, the projected cost to SOCs nearly doubled during the same period, exceeding an average $8.1 million on an annualized basis. For US-based companies, this matters—a lot. Today, a successful phishing attack can lead to losses of as much as $1.6 million. If it results in a data breach, costs skyrocket to an average of $7.9 million per incident.
According to Ponemon Institute, the probability of falling victim to a breach is now 14% per year. And it's getting worse—in part because of the very mechanisms businesses are putting place to mitigate the issue.
The Downside of Employee-Reported Phishing
The fact is, even with today's most advanced threat protection solutions in place and the best security awareness training available, there is no possible way to completely remove the risk that an employee will fall for a phishing email designed to defraud the company or steal sensitive information as part of a data breach.
As part of our quarterly reports, ACID surveys SOC professionals at 280 large organizations to get a read on the state of incident response in a rapidly evolving threat landscape. In addition to security awareness training and phishing simulations, this quarter's survey finds that 95% of businesses have implemented solutions that give employees the ability to report suspected phishing emails. But all too often, employee-reported emails end up flooding SOCs with more incidents to triage, investigate, and remediate than they can handle.

What's more, nearly 56% of all those reported incidents are false positives. That's up 7% in the US, and 10% globally, in just three months. Combine it with the increased volume of employee-reported incidents overall, and a number of significant challenges become immediately apparent.
As just one example, the new 2019 Verizon Data Breach Investigations Report finds that in 40% of all breaches, data exfiltration begins within minutes. Unfortunately for everyone involved, it takes most companies months or even years to discover them and even longer to repair the damage. With employee-reported phishing attacks rising rapidly, the distance from breach to remediation is likely to grow worse.
SOC Costs Skyrocketing
In the face of all of this, the number of SOC analysts per organization hit 14.5 in Q1. The good news is that is a 16% increase from the previous quarter.
Specific numbers can vary widely based on the size of the organization or the total volume of phishing attacks. Approximately 41% of organizations with more than 10,000 employees have 20 or more SOC analysts. The same applies to those hit with 60,000 or more phishing incidents annually, no matter the size of the company. Yet while rising analyst headcounts are encouraging, a persistent SOC staffing gap continues to grow more precarious.
Based on the average number of incident reports and the amount of time it takes to remediate them, SOCs would need 90 analysts to handle the number of reported phishing incidents they receive each year. That represents $8.1 million in annual staffing costs—up 200% in just three months.
On average, that means SOCs need to hire 76 full-time equivalents to avoid the heightened risk of data breach and fraud. But for many, there is a far easier solution.
Automation in the Spotlight
According to this quarter's survey results, SOC professionals estimate that they could reduce their company's breach risk an average of 51% by automating phishing incident response processes. In fact, that could have a cascading effect that could dramatically lower SOC costs overall.
To solve this exact problem, Agari Phishing Response is a one-touch automation solution that has been shown to reduce the time needed to triage, investigate, and remediate phishing incidents by as much as 90% in real-world implementations. As a result, security teams can ignore false positives and focus on real attacks. Furthermore, breaches can be identified and contained in mere minutes instead of months, helping SOCs save time while helping their organizations avoid millions in potential losses.
Applying the SOC analyst's estimated reductions across the data captured in the Q2 report, it's possible to estimate that a solution such as Agari Phishing Response could help organizations realize $7.29 million in SOC analyst time savings relative to estimated staffing requirements. They can also pocket another $561,025 in savings from that 51% reduction in breach risk. The grand total: an average $7.85 million in annual savings.
No Letting Up
There have already been more than 281 significant data breaches so far this year, and they aren't slowing down. Yet despite all the risks, nearly 20% of IT and security leaders say their organizations are more vulnerable to data breaches than they were in the preceding 12 months. Indeed, the targeted phishing attacks that can lead to such breaches rank as the #1 cybersecurity threat organizations face today. Which means finding new ways to automate and accelerate phishing incident response times is more important than ever.
To learn more about trends in phishing incident response, download a copy of the Q2 2019 Email Fraud and Identity Deception Report.