Defend Your Brand's Domains with Fortra's Agari DMARC Protection Solution
Email remains a popular convoy for threats such as phishing and impersonation. DMARC is an email authentication protocol that helps identify and quarantine malicious emails, and prevents fraudulent use of legitimate brands. Learn more >
How Does DMARC Work?
We know DMARC is a technical standard that helps prevent spam and email spoofing, but how exactly does it work?
DMARC allows domain owners to publish their email authentication policies, and dictate what happens to inbound messages that fail those series of authentication checks. DMARC utilizes the authentication standards of SPF and DKIM to provide better security through the SMTP protocol.
Let’s break down how an email message would be validated through DMARC.
Publish the DMARC policy.
The owner of the domain publishes a DMARC record that outlines its email authentication policy. This record is stored on the domains DNS server.
The owner of the domain publishes a DMARC record that outlines its email authentication policy. This record is stored on the domains DNS server.
Mail servers check inbound mail using DNS.
The recipient mail server checks for a DMARC policy using the “From” header in the sender's message. This checks the message for a valid DKIM signature, a matching IP address in the senders SPF record, and tests for domain alignment.
The recipient mail server checks for a DMARC policy using the “From” header in the sender's message. This checks the message for a valid DKIM signature, a matching IP address in the senders SPF record, and tests for domain alignment.
Apply the DMARC policy.
The server uses the results of these checks to apply the domain's DMARC policy. This can either accept, reject, or quarantine the email.
The server uses the results of these checks to apply the domain's DMARC policy. This can either accept, reject, or quarantine the email.
Generate a DMARC report.
The receiving mail server sends a report detailing the outcome of the email, and any other messages sent from the same domain. DMARC aggregate reports are sent to the email address specified in the DMARC record.
The receiving mail server sends a report detailing the outcome of the email, and any other messages sent from the same domain. DMARC aggregate reports are sent to the email address specified in the DMARC record.
Benefits of DMARC
DMARC is a free way for anyone to implement email security at the protocol level. Unlike security plugins, DMARC works on the DNS level to protect inboxes. Implementing DMARC on your mail server has numerous benefits that can:
DMARC stops attackers from sending fraudulent messages from your domain. A DMARC record provides anti-spoofing protection by using DomainKeys Identified Mail (DKIM) and Sender Policy Framework (SPF) record checks to validate messages. Domain owners can then set policies to dictate what happens to messages that fail these checks.
According to Verizon’s 2023 Data Breach Investigations Report, Business Email Compromise (BEC) almost doubled in incidents from November 2021 – October 2022, and represent more than 50% of total social engineering ploys. In addition, the 2023 FBI IC3 report listed phishing as the most common cybercrime, with nearly 300,000 complaints in 2023, which was 5.35x more than the next largest attack type.
With email-based threats showing no sign of slowing down - in fact, they're increasing every year - all signs point toward implementing a DMARC domain protection solution if you don't have one already.
DKIM & BIMI Records
DKIM
DKIM, Domain Keys Identified Mail, is a technique that uses your domain name to sign your emails with a digital “signature” so your customers know it’s really you sending those emails and that they haven’t been altered in transit.
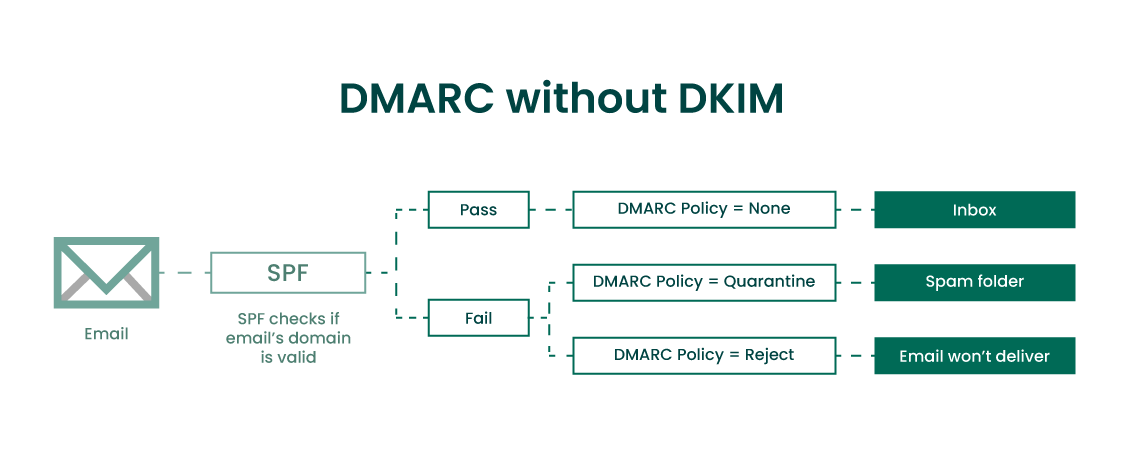
Can I Use DMARC without DKIM?
The short answer is yes, you can use DMARC without DKIM. By using SPF authentication you can set up DMARC without having a DKIM record. When using SPF you create a rule that states DMARC authentication passes as long as the SPF check is valid and the SPF identifier is aligned.
But what if SPF authentication fails? Legitimate messages can fail SPF validation when they are forwarded, and the intermediary IP address is not listed on the SPF record.
If DMARC is using only SPF for validation, that legitimate message being forwarded will be rejected by the DMARC policy. Having DKIM as a part of your DMARC setup helps eliminate that problem by having an extra set of authentication checks present.
A full DMARC implementation with SPF and DKIM working together is your best bet. Having both SPF and DKIM configured improves your chances of legitimate email passing DMARC authentication. Read how to set up DKIM >
Monitoring your DMARC reports using a “none” policy helps give administrators a look into who is forwarding emails on the domain’s behalf. If you’re thinking about implementing DMARC without DKIM, consider monitoring your DMARC reports closely before switching to “quarantine” or “reject” policy.
BIMI
Brand Indicators for Message Identification (BIMI) is a newer standard that attaches your brand logo to authenticated emails sent from your organization. This helps build both trust with your subscribers, as well as brand awareness.
Implementing BIMI can help recipients visually verify that the message is legitimate since the branded logo is only applied to the email if it has passed DMARC authentication.
Can BIMI be used with DMARC?
Yes, BIMI can only be implemented once DMARC authentication is active on a domain. BIMI is often viewed as an extension of DMARC that helps brands build trust and awareness with their audience via email. Read how to set up BIMI >
Steps to Create Your DMARC Record
While you don’t need DMARC to send emails, it’s one of the best forms of protection against domain impersonation attacks. When you set up DMARC, you’re protecting all emails sent from that domain. This makes creating a DMARC record a fast and scalable way to protect an entire organization in a single afternoon.
Getting Started
Before creating a DMARC record, you’ll need to have both SPF and DKIM authentication active on your server for at least 48 hours before setup.
Use the Agari DMARC Setup Tool and enter the name of your domain into the search field and hit Submit. If your domain does not have a DMARC record already created, you should see the option to “Create DMARC Record.” If your domain already has a DMARC record created, you should see the existing record and an option to "Modify DMARC Record".
If you're ready to get started click to button appropriate for your situation.
Creating Your DMARC Record
Here you’ll be able to specify the policies you want for your DMARC record. If you’re unsure of how strict you want to make your DMARC policy, start with Monitor Only as this will not impact mail flow and can always be changed later. By using Monitor Only you will set your DMARC policy to “none.” This will allow you to review your DMARC report and then change that policy to “quarantine” or “reject”.
Next, specify a valid email address for your Aggregate Reports and Forensic Data to be sent to. This should be a separate inbox dedicated to collecting DMARC reports.
Click Next. On the next page, you should see your DMARC record that includes all the policies and settings you requested. Your record should look something like:
V=DMARC1; p=none; rua=mailto:[email protected]
Copy your record and save it.
Creating Your TXT Record
Next, login to the admin panel of your DNS hosting provider. Each provider has a different layout, but all will have the option to add a new DNS record. Create a new DNS TXT record.
For the record type choose TXT.
Under the Host Value section enter “_dmarc” as the Host without quotes.
In the TXT Value box paste the record you copied earlier. Make sure changes are saved and applied.
Validate Your New DMARC Record
After a few minutes, head back to the Agari DMARC Setup Tool and check your domain again. You should now see that your DMARC record was found. DMARC reports may take longer to populate. If reports don’t appear, allow 24-48 hours for your DNS settings to propagate.
Types of DMARC Policies
There are three main policies that can be specified in your DMARC record. These determine what happens when that message fails the DMARC check. Those policies are:
Both “reject” and “quarantine” offer protection against spoofed messages. Larger organizations often set their policy to “none” and then monitor their DMARC report. The report will help administrators get a better understanding of how mail flows from their domain, and help them choose the best policy that won’t impact legitimate traffic.
Individual recipients can choose whether or not they want to ignore DMARC policies set by the sending domain. Many email security applications offer features that allow organizations to customize their spam filter settings.
These filters can be set to ignore DMARC/DKIM misalignments or failures. Emails can also be tagged in the subject line and sent to its destination, rather than being completely rejected.
Agari can demystify DMARC for you!
GET GUIDE
Why Does DMARC Fail?
DMARC can fail if the record is misconfigured, or if the domain is already being spoofed by attackers. Let’s review some of the most common reasons why DMARC fails, and how to remedy it.
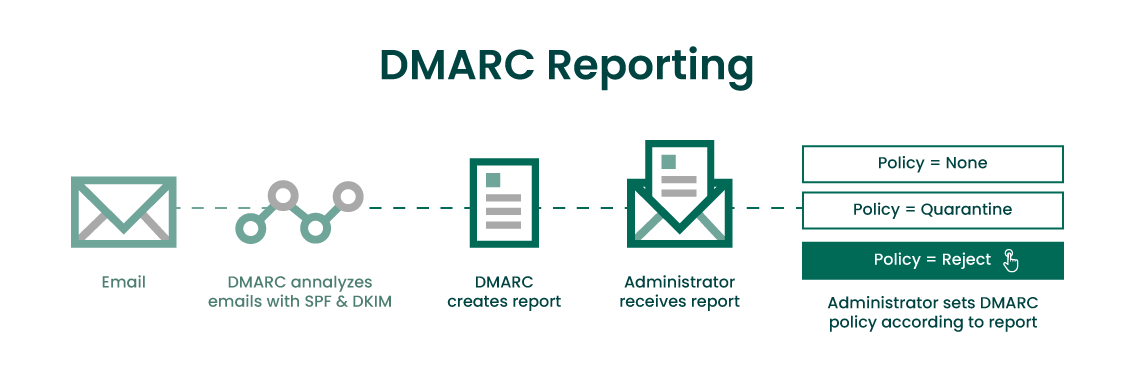
Checking Your DMARC Reports
DMARC reports are valuable, and allow you to see which emails on your domain are passing DKIM, SPF, and DMARC checks. Monitoring your mail flow from your DMARC report allows you to update your DMARC policies with stricter enforcements gradually, further strengthening your protection against spoofing attacks.
There are two types of DMARC reports, DMARC Aggregate reports (RUA) and Forensic DMARC reports (RUF).
DMARC Aggregate Reports (RUA): Contain information regarding the authentication status of messages sent on behalf of your domain. These reports show which messages are passing DKIM and SPF validation, and which ones are not.
These record details such as the domain that used to send the message, the IP address the message was sent from, the date, and the result of the DKIM/SPF policy check. These reports can identify spoofing attempts as well as outline future “reject” policies.
DMARC Forensic Reports (RUF): Contain information when an email sent through your domain fails either DMARC, SPF, or DKIM validation. Similar to RUA reports, these logs contain key details that allow you to identify the source of these messages and fix the issue. RUF reports are valuable for both troubleshooting deliverability issues, as well as identifying sending IP addresses of attackers who are actively attempting to spoof your domain.
It’s common practice for organizations to start off with their DMARC policy set to “none”, and then change it to “quarantine”, and finally “reject”. This strategy gives you time to fully review your DMARC report, and make those changes without the risk of accidentally impeding legitimate mail flow.
It’s best to set up a dedicated mailbox specifically for DMARC reports. This helps keep the reports organized and doesn’t overwhelm a shared inbox with a flood of messages. Reports are generated based on how much email your domain sends. Enterprise organizations may see several hundred DMARC reports per day.
Limitations of DMARC
While it’s true DMARC is the best defense against email spoofing, there are some limitations as to what DMARC can do in terms of email security. Let’s compare what DMARC can and cannot do.
DMARC can help organizations:
- Reduce the amount of spam they receive
- Stop their domain from being spoofed
- Prevent emails from being tampered with in transit (when using DKIM)
- Understand who is sending messages from a particular domain
- Prevent phishing attacks from reaching user inboxes
- Use DMARC reports to understand how attackers are trying to use their domain
DMARC cannot:
- Scan emails for malicious content
- Prevent phishing attacks that use look-alike or cousin domain attacks
- Detect and removing malicious links inside of emails
- Monitor the content of inbound or outbound messages
Get Started
Email Protection From The Founders of DMARC
Agari offers a turnkey solution to combat email threats using both DMARC and advanced phishing protection. This combination stops both domain spoofing attacks as well as phishing attacks that use misspelled domain names.
Predictive analytics identifies new threat trends as they emerge by proactively scanning trillions of messages. As new threat patterns are identified, they are automatically applied to your threat database, ensuring even the newest types of attacks are thwarted.
No matter where your email is hosted, Agari offers a wide variety of integrations into platforms like Office 365, Microsoft Exchange, and Gmail. Setup is simple and doesn’t require any downtime, meaning no missed emails during onboarding.
Agari works to ensure DMARC is configured properly and fills the gaps where DMARC falls short. Agari DMARC Protection automatically implements a full DMARC solution for you, even if you’re starting from scratch. The system scans the web and your DMARC reports to proactively identify and shut down spoofing attempts and lookalike domain attacks.
Schedule a live demo of
Agari DMARC Protection
Read our comprehensive guide:
"Getting Started with DMARC”
Look up or generate your
DMARC record with our free tool.