With 60 million corporate employees working remotely due to the Coronavirus outbreak, cybercriminals are switching up their tactics in business email compromise (BEC) scams.
In what has been called the "world's largest work-from-home experiment," organizations around the globe are being forced to quickly transition to a remote workforce, ready or not. Cybercriminals have opportunistically adjusted to this new normal by updating phishing lures, malware, and other fraud techniques. BEC crime rings are no different.
Impersonation scams rely on gift cards as a cash-out method. In fact, gift cards are the most popular tool that fraudsters use to advance the scam from email message to fiat currency. All a threat actor needs to do is ask unsuspecting victims to send them a picture of the physical gift cards, which can then be sold for roughly 70% of face value in bitcoin.
This tried and true method is a gateway for laundering money and it isn't just for BEC gangs, either. The tactic is widely used by state-sponsored threat actors such as Lazarus Group, the North Korean APT group behind Wannacry, to skirt US sanctions. But in the age of shelter-in-place orders and quarantines, this approach won't cut it anymore.
BEC By Text Message: 'Can You Run a Quick Errand?'
Before COVID-19, gift card scams were relatively straightforward. BEC actors would impersonate a company's CEO or another senior executive in email requests asking a targeted employee to purchase physical gift cards.
The reasons given included a party for fellow team members, a vendor who needed to be paid in gift cards, or a bonus for specific staff members for outstanding performance during the past year.
Along the way, the fraudster would invariably ask the employee for their mobile phone number, ostensibly so they could communicate back and forth. By moving the conversation to SMS, scammers are able to bypass email protections and get a photo of the gift cards.
In almost every case, perpetrators would ask the employee to run to a store to purchase between $500 and $1,000 worth of gift cards. And it works. According to our latest email fraud trends report, gift card scams account for 62% of all business losses attributed to BEC attacks. That could represent more than $5.2 billion in business losses worldwide this year.
Faced with a newly remote workforce and shuttered stores due to the current crisis, BEC groups have suddenly needed to find a way to keep these sizable revenue streams flowing. And it looks like they may have found one. Example: BEC email referencing employees working from home.
Example: BEC email referencing employees working from home.
Going Remote: Gift Card Laundering When Stores Are Closed
Up until now, victims conned into going to the store and purchasing gift cards were instructed to scratch the back of the cards off and send a photo to the scammers. Needless to say, there are a lot of steps to this scam that could raise suspicions. But now, fraudsters have turned to digital gift cards, which come with a big upside - higher payouts.
 Example: BEC email requesting online gift cards.
Example: BEC email requesting online gift cards.
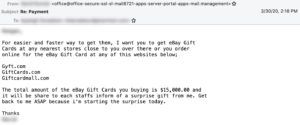
For in-store gift card purchases, most retailers attempt to curb fraud by limiting the number of cards that can be purchased in one transaction. But online retailers don’t seem to have the same restrictions. One BEC group we track that usually requests checks from BEC victims—a gang we've code named Exaggerated Lion—has recently included gift card requests in their repertoire, asking for as much as $15,000 in “surprise” gift cards for employees.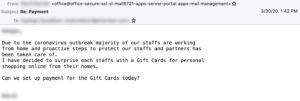 Example: Exaggerated Lion BEC email requesting $15,000 in gift cards.
Example: Exaggerated Lion BEC email requesting $15,000 in gift cards.
Plenty of Scams In Store—and Out
BEC scammers haven't written off real world stores completely, mind you. They just changed their targets. After much of the US went into lockdown, gift card fraudsters shifted away from large retail stores such as Target and Walmart, and toward local pharmacies such as CVS and Walgreens, as well as other businesses deemed "essential."
 Example: BEC email referencing specific “essential” store for a target to buy gift cards.
Example: BEC email referencing specific “essential” store for a target to buy gift cards.
While we don’t yet have concrete evidence about how these stores come into play, it seems a safe assumption that victims asked to buy gift cards either comply, or are refusing to venture out and are instead looking for safer alternatives to make the purchase. The safest way for the scammers to cash out is through digital gift cards, and they just started doing it.
Trying to track the money chain from these crimes is extremely difficult, if not impossible, due to the lack of a networked gift card tracking system. And with virtually no limits on purchase amounts, this cash-out method is sure to catch on—while losses add up fast.
To learn more about gift card scams and other BEC email attacks, read the Q1 2020 Identity Deception and Fraud Trends Report from Agari.



