In 2021 alone, the FBI's IC3 report published that over $44 million in losses were a direct result of effective phishing and advanced email scams. The Agari Cyber Intelligence Division analyzed trillions of emails and nearly 500 million Internet domains to uncover the scope and impact of this email fraud… and the trends that benchmark enterprise security teams’ ability to respond to email threats.
This report delivers data and key findings from the second half of 2021 regarding DMARC enforcement trends and concluded that:
- The world’s largest and most prominent companies are leading the charge of setting DMARC levels at full enforcement, however nearly two-thirds of Fortune 500 companies STILL remain vulnerable to getting impersonated in scams that target their customers, partners, investors, and the general public
- The Brand Indicators for Message Identification (BIMI) boom is a boon for the entire email ecosystem by validating emails from consumer companies with verified brand logos in recipients’ inboxes
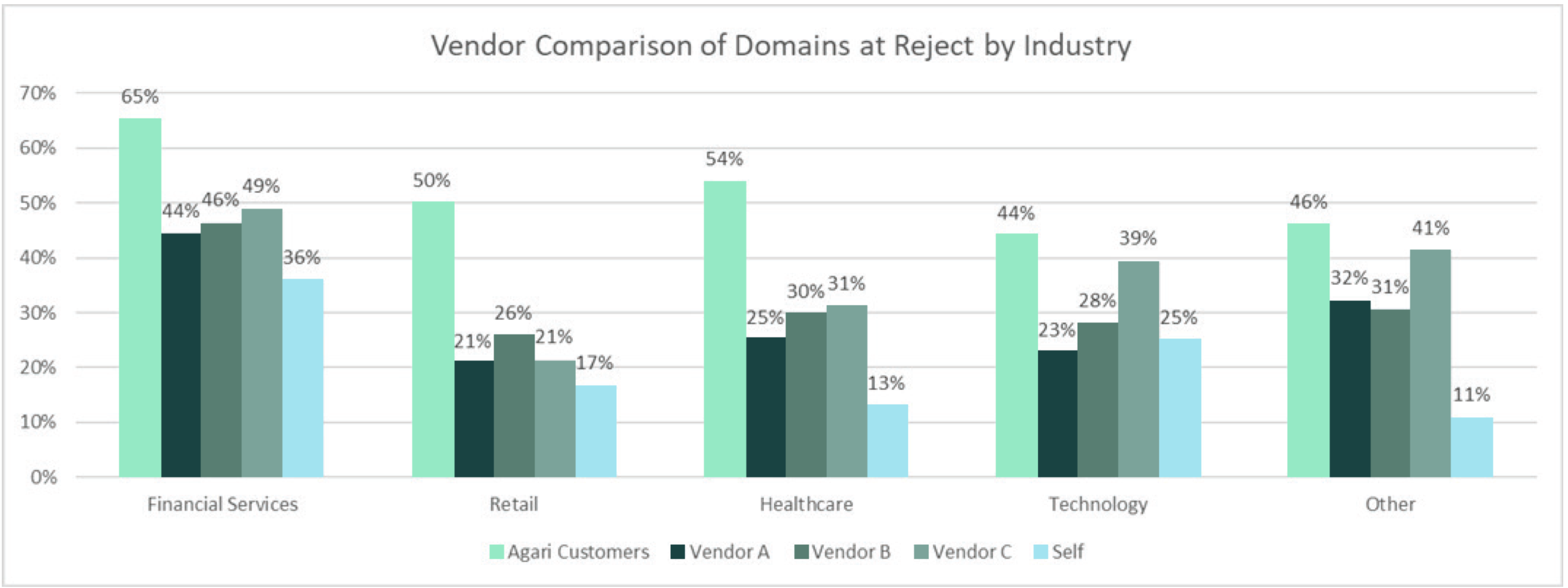
- DMARC adoption rates increased steadily in 2021 across most key industries, including financial services and healthcare, to technology and SaaS providers (and Agari customers are way ahead of the masses!)
- And more!
Image
Arm yourself with this essential data and intelligence by downloading the
“2022 Email Fraud & Identity Deception Trends: The State of DMARC Enforcement”
report today!