Organizations are more likely to be breached today than ever before, as cybercriminals shift tactics once again, using account takeovers (ATOs) to launch targeted email attacks. In fact, a recent Osterman Research survey reported that one in five organizations fell victim to an ATO-based email attack within the past 12 months. Attackers know that trusted email is the most effective way of breaching an enterprise, as existing security controls cannot detect these attacks since they come from previously established credible senders.
Meanwhile, employees have a hard time spotting these attacks because they appear to come from trusted colleagues. As such, organizations must place a higher priority in protecting against account takeovers—or risk becoming the next victim.
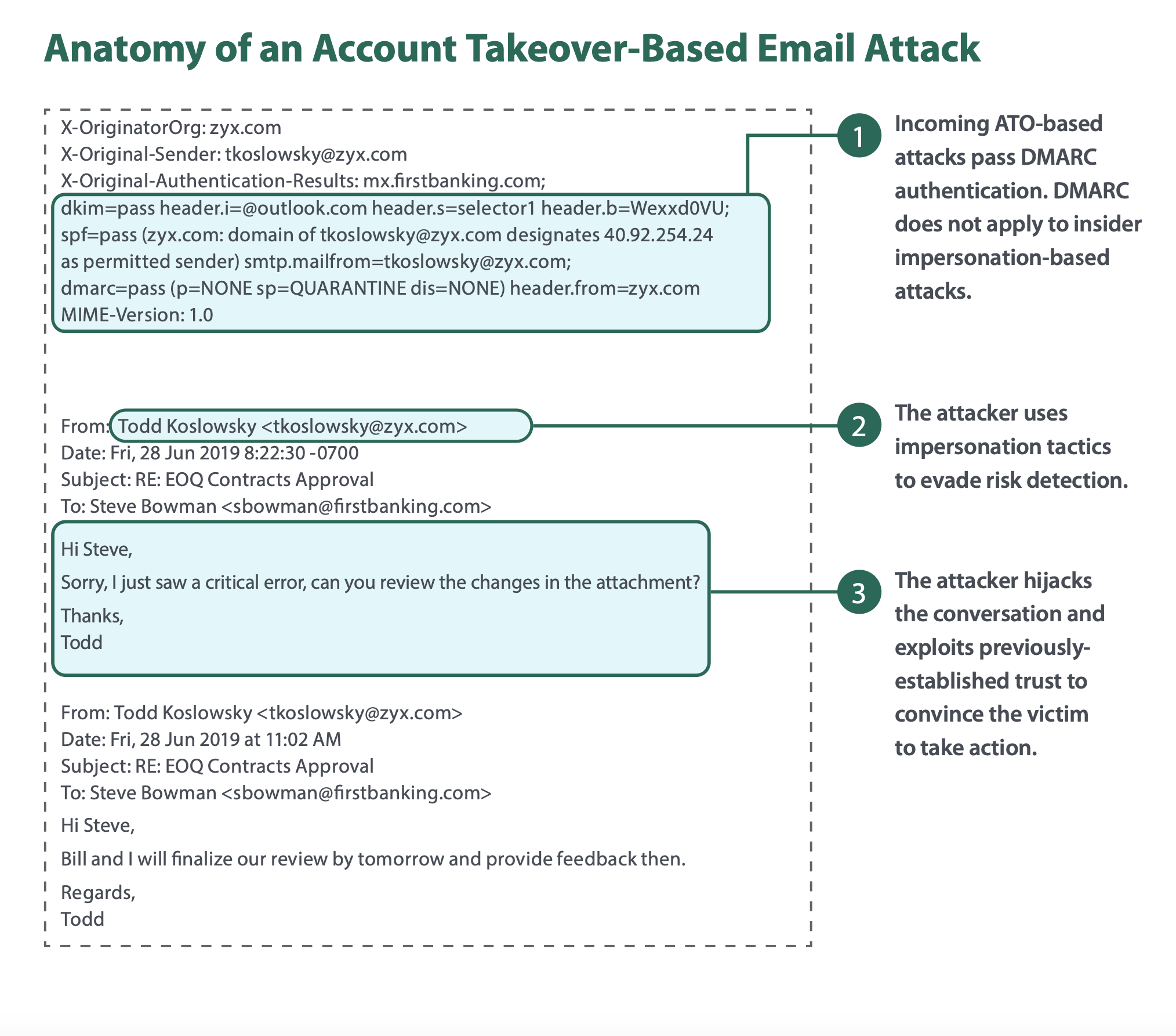
Introducing Email-Based Account Takeover Attack Prevention
Fortra's Cloud Email Protection prevents email-based account takeover attacks from reaching employee inboxes. It also inspects email flowing within an organization for indicators that an internal email account has been compromised for unauthorized use. Once an account takeover is suspected, Cloud Email Protection prevents the spread of malicious emails from affected accounts laterally within and externally to the organization.
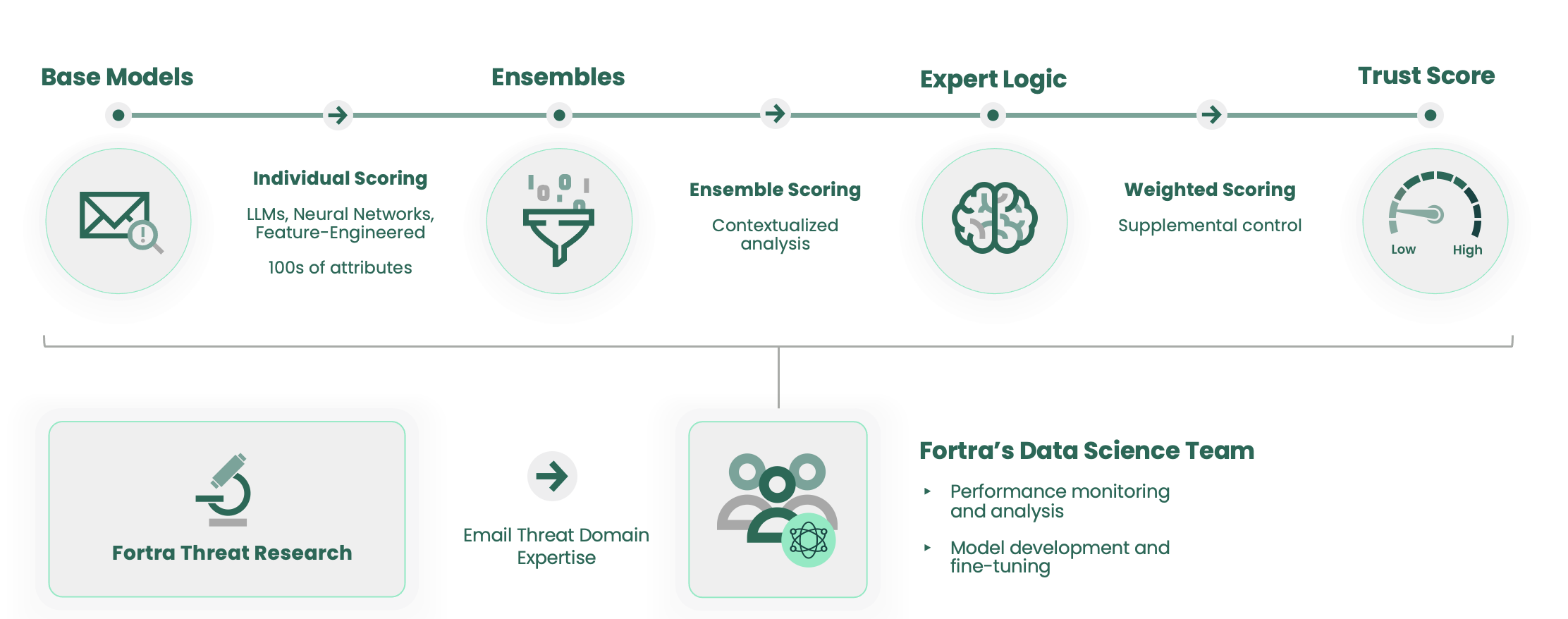
The Science Behind the Scenes of Cloud Email Protection
Fortra’s Advanced Data Science employs a combination of machine learning, large language models, and neural networks to determine whether an email should be trusted. It quickly detects and stops advanced impersonation threats, like BEC, that bypass signature or pattern-based defenses, before reaching user inboxes. By analyzing hundreds of email characteristics and header data, Fortra’s Advanced Data Science models scan and interpret internal employee-to-employee messages to detect malicious attachments and URLs sent from compromised internal accounts, as well as prevent ATO-type attacks that originate outside of an organization.
The advanced system of machine learning (ML) models work together to accurately detect impersonation and social engineering techniques used in messages. Comprised of data scientists with extensive experience in practical applications of modern ML and AI technologies, Fortra’s Data Science team has developed high-performing models that consider parts of messages and contextual data both individually and collectively. These models are combined using ensemble learning techniques that relate them to one another to consider all threat characteristics and patterns and attach a score to each while applying expert logic-based rules. Together, all of these steps maximize email legitimacy confidence and ensure accuracy.
Benefits of Implementing Fortra's Cloud Email Protection
With the increased effectiveness of exploiting account takeovers over existing techniques, rising financial gains, and lack of organizational protections, attackers are highly motivated to increase their attack rate in the coming year. With Cloud Email Protection, organizations will have the prevention capabilities needed to stop these attacks—ensuring critical-business communication continues to flow securely and uninterruptedly.
In the past year, we have seen a 300% increase in the number of compromised accounts sending advanced email attacks into the organization and we see stopping this threat as a critical security control.
CSO Large Healthcare Organization