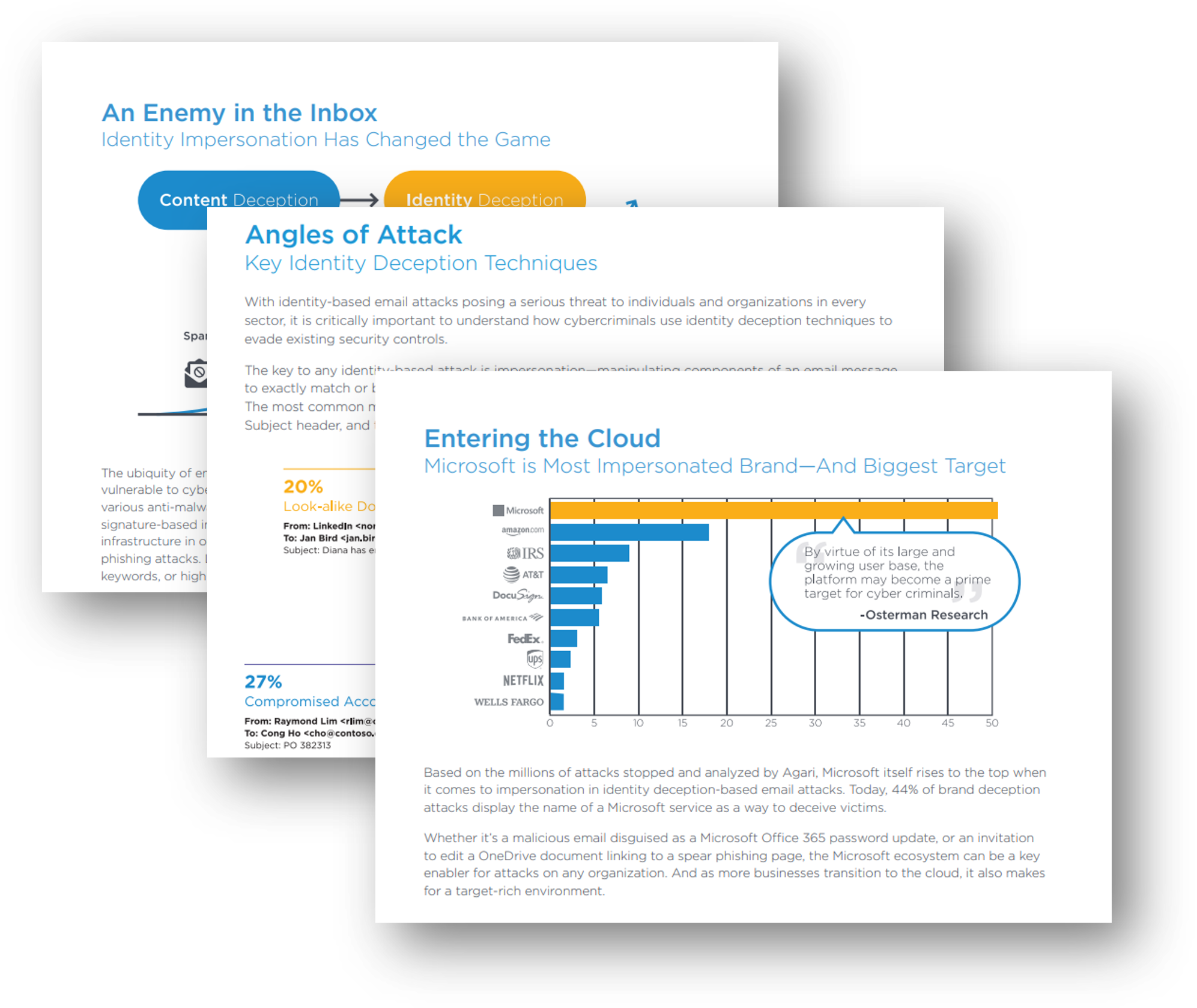
The secure email gateway worked for years, but it is no match for a new generation of rapidly evolving advanced email attacks that use identity deception to trick recipients.
Download the white paper to learn about the next-generation Secure Email Cloud Architecture, including:
- What cybercriminals are doing to successfully scam people and organizations
- How Microsoft 365 and other cloud-based email have the same functionality as a SEG
- Why Agari and Microsoft 365 are all you need to protect your organization from threats
Image