You've Got Microsoft Office 365 Email Security–But Has Your Architecture Caught Up to Catch Advanced Email Attacks?
Secure Email Gateway (SEG) appliances tend to present an obstacle to cloud-first strategies by sitting “inline” as email passes through. By doing so, on-premise SEGs alone muddle Microsoft 365’s (M365) Exchange Online Protection’s native features, preventing optimal function and diverting the feedback loop from users directly to the SEG, leaving it unaware of user-reported phishing attempts.
In turn, many Microsoft Office 365 Email Security customers eliminate the Secure Email Gateway (SEG) appliance and add Exchange Online Protection with Microsoft Defender for Office 365 to stop spam, malware, and more. However, this still leaves organizations vulnerable to advanced email attacks that leverage impersonation tactics, such as:
Business Email Compromise

Eliminate fake email messages from imposters posing as trusted colleagues, associates, and friends to defraud your business. Learn more >
Spear Phishing

Prevent executive impersonation and other highly targeted identity deception schemes designed to steal funds and obtain confidential information. Learn more >
Account Takeover

Stop targeted email attacks originating from a compromised email account, exploiting the previously established trust between the compromised sender and their contacts. Learn more >
Social Engineering
Outsmart organized crime rings that use social engineering to manipulate employees into divulging information and performing other harmful actions. Learn more >
Shroud Any Gaps in Email Security with the Cloud
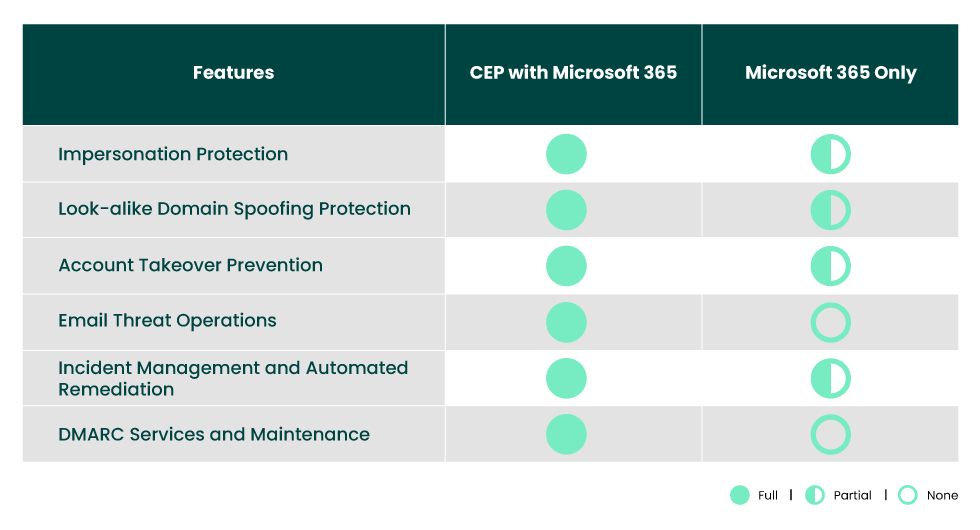
Fortra's Cloud Email Protection fortifies Microsoft Office 365 Email Security simply, cost-effectively, and efficiently while stopping:
• Business email compromise and spear phishing attacks
• Low-volume, highly targeted attacks using impersonation
• Socially engineered attacks with no malicious content
• Spam attacks missed by Microsoft 365 Email Security
Integrates Easily with Microsoft Office 365
Fortra’s Software-as-a-Service (SaaS) solutions offer an off-the-shelf connectivity to Microsoft 365. Combined together, Fortra’s Advanced Email Security solutions and Microsoft 365 provide a single integrated architecture for detection, prevention, and remediation of all types of advanced email threats that leverage identity deception tactics.
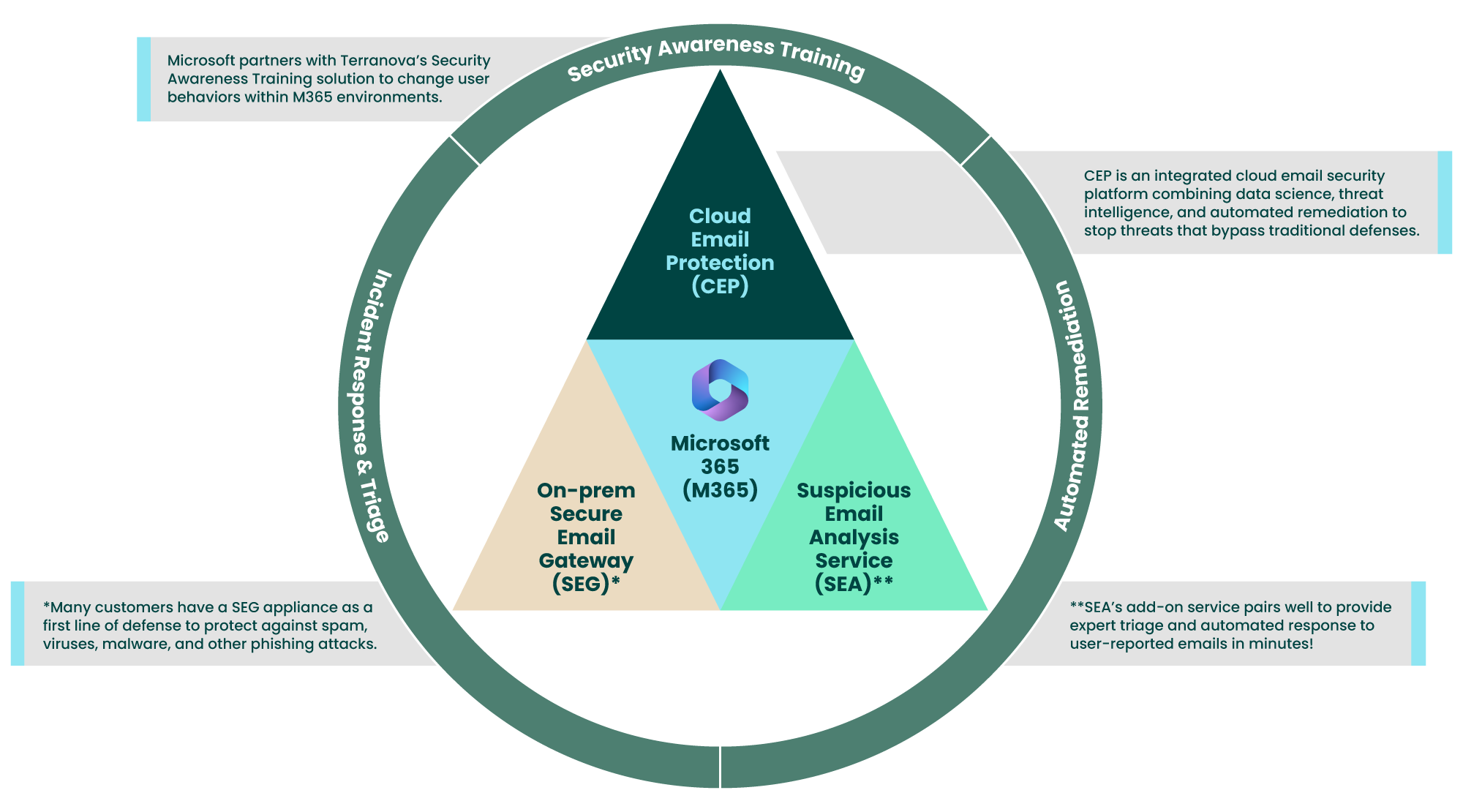
Security Awareness Training (SAT)
Supplement Your Security Awareness with Simulations
Learn More
Supplement Your Security Awareness with Simulations
Secure Email Gateway (SEG)
Fortify Your DLP Defenses with a SEG
Learn More
Fortify Your DLP Defenses with a SEG
Cloud Email Protection (CEP)
Download the Data Science Details
Learn More
Download the Data Science Details
Suspicious Email Analysis (SEA)
SEE What SEA Can Do for You
Learn More
SEE What SEA Can Do for You
How Do Organizations Mitigate These Threats?
Ravisha Chugh, Product Marketing Lead at Fortra and former Senior Principal Analyst at Gartner, recommends employing “. . . email security solutions that include anti-phishing technology for targeted BEC protection that use AI to detect communication patterns and conversation-style anomalies. . .” It also promulgates “select products that can provide strong supply chain and AI-driven contact chain analysis for deeper inspection and can detect socially engineered, impersonated, or BEC attacks.”
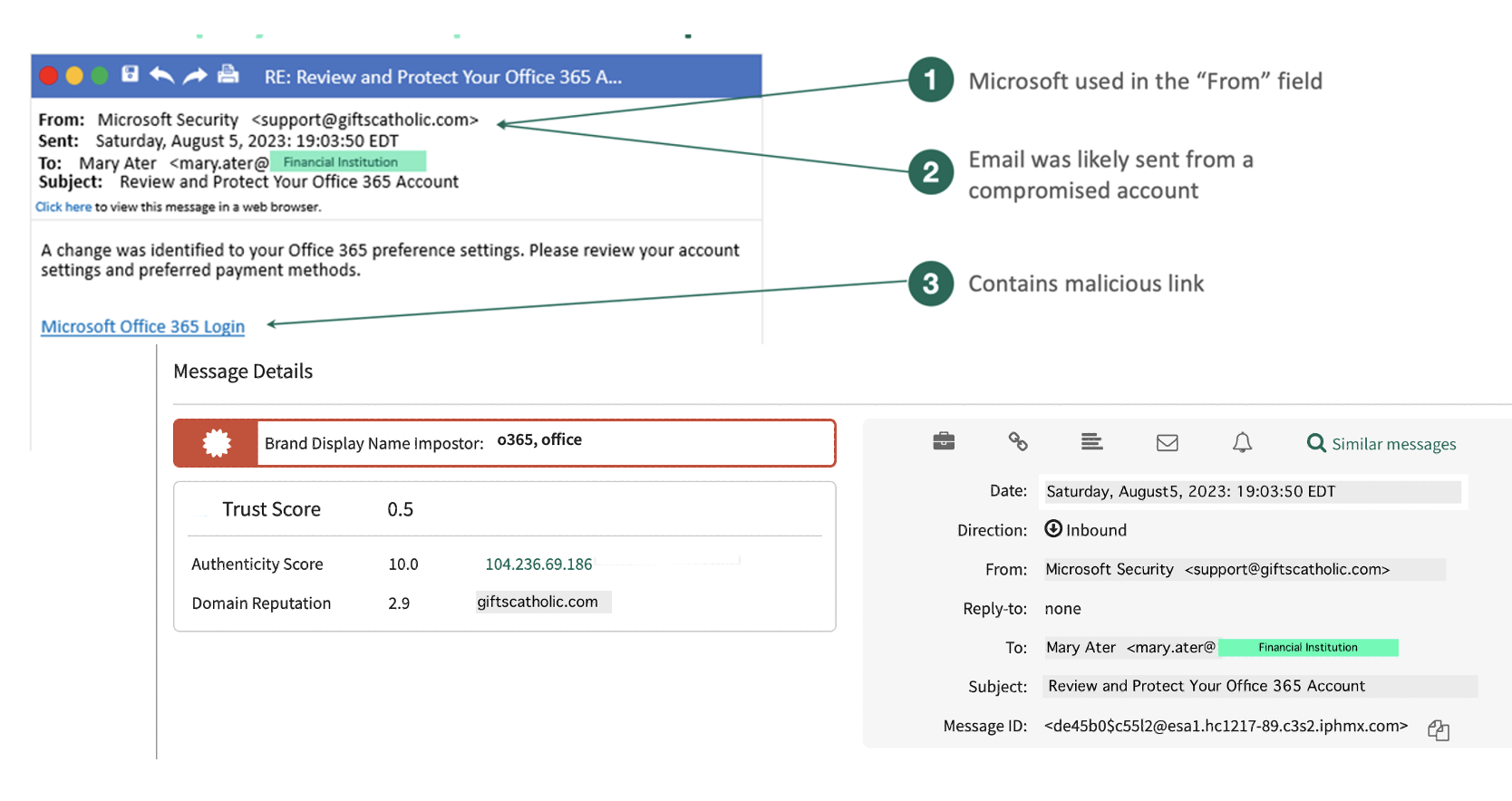
In simpler terms, enterprise organizations need an extra layer of defense to augment Office 365 Email Security for sophisticated threats that bypass SEGs or other legacy security defenses, such as this Office 365 lure:
Benefits of Augmenting Microsoft Office 365 Email Security with Fortra's Cloud Email Protection
Solutions
Protect Your Organization from Costly Advanced Email Attacks
Fortra Advanced Email Security solutions can be deployed alongside Microsoft Office 365 Email Security packages to ensure your organization’s valuable information remains secure — whether it’s housed on-premise, in the cloud, or a hybrid version.
