What is the difference between SMTPS and SMTP?
SMTPS uses additional SSL or TLS cryptographic protocols for improved security, and the extra "S" stands for SECURE!
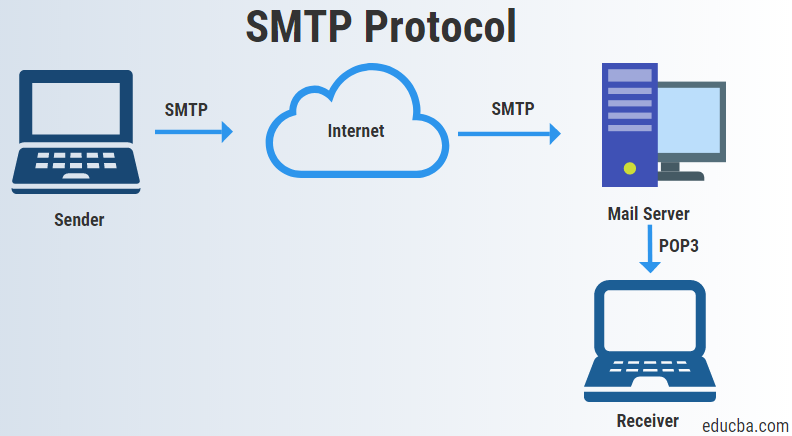
By default, SMTP to send email lacks encryption and can be used for sending without any protection in place, leaving emails with an SMTP setup susceptible to man-in-the-middle attacks and eavesdropping from bad actors while messages are in transit. Read more about Agari's anti-encryption solution that wards off Ransomware.
In contrast, SMTPS utilizes either TLS or SSL to secure email communications using asymmetric cryptography. The main takeaway is that just an SMTP setup is susceptible to attacks, while SMTPS secures the connection by leveraging TLS for email.
What is an SMTP injection attack?
Email that is not secured using SMTPS is vulnerable to a series of attacks that can modify the contents of a message or reroute that message to an attacker before being passed on to the intended recipient. Read the latest article from HelpSystems' cybersecurity expert, Eric George, on persistent ransomware and the importance of encryption.
Attackers exploit the unencrypted communications by injecting their own malicious SMTP commands into data as it is transmitted from a server. Attacks like these, such as those that feature contact forms (that are rife with built-in vulnerabilities) can be used to send spam from the vulnerable domain, steal sensitive information silently, or to conduct phishing attacks.
How is SMTPS enabled?
Secure SMTP can be achieved through the enablement of TLS on your mail server. By enabling TLS, you are encrypting the SMTP protocol on the transport layer by wrapping SMTP inside of a TLS connection. This effectively secures SMTP and transforms it into SMTPS.
Port 587 and 465 are both frequently used for SMTPS traffic. Port 587 is often used to encrypt SMTP messages using STARTTLS, which allows the email client to establish secure connections by requesting that the mail server upgrade the connection through TLS.
Port 465 is used for implicit TLS and can be used to facilitate secure communications for mail services. According to the Internet Engineering Task Force, or IETF, this is preferred over using STARTTLS on port 587.
Lastly, port 2525 is sometimes also used. Some residential ISPs will block port 25 to stop users from running their own mail servers. To combat this, enthusiasts and small home businesses use port 2525.
System administrators can enable SMTPS through the client settings on their SMTP connector. This step will vary depending on which mail server you are running. For example, when configuring the connector in Outlook, there are options for setting the authentication type where SMTP TLS will be an option.
How do I know if my emails are using SMTPS?
You can check to see if your emails are being sent securely by viewing the headers of the email in question. This can be done in most modern email clients. In Outlook, this can be done by doing the following:
Open the email you wish to check the security of.
Navigate to File tab > Properties. This will open up the email header information which will contain transmission information, including encryption details if they are being applied.
For Gmail users the process is a bit easier. To check if the email is being sent via SMTPS simply open the email in question and click the small arrow next to your name underneath the sender's address. You should see something like this:
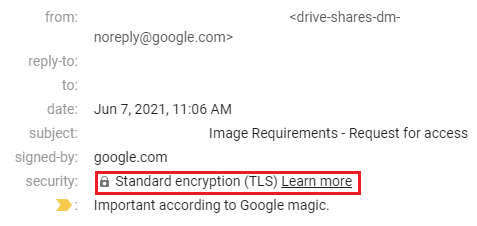
The security tab will provide details about the type of encryption used to secure the email, along with the domain that signed the certificate above it.
Does SMTPS protect against all email threats?
SMTPS plays a key role in email security, but it can’t protect against all email-based threats. Emails using SMTPS are protected against:
- Man-in-the-middle attacks
- Messages being read by attackers while in transit
- Messages being forwarded to attackers
SMTPS does NOT protect against:
- Phishing attacks that use lookalike domains
- Malicious attachments that contain viruses
- Links inside of emails that redirect to malicious sites
- Emails that use social engineering to trick recipients into sharing sensitive information
- Servers sending spoof emails from domains that they do not control
Other forms of email protection
Secure SMTPS keeps messages from prying eyes while in transit. But what about spoofing, and phishing, and spam? OH MY!
Let’s take a quick look at a few email standards you can deploy to protect your email and domain:
Sender Policy Framework (SPF): Helps recipients of your messages verify that messages from your domain are in fact coming from you. SPF tells the world which servers you send email from. If a message is sent from your domain that does not originate from these servers, the SPF check fails.
Domain Keys Identified Mail (DKIM): Provides an extra layer of email authentication by giving the messages a digital signature. DKIM helps prevent messages from being tampered with while in transit.
Domain-based Message Authentication Reporting and Conformance (DMARC): Authenticates messages by aligning SPF and DKIM capabilities. Having DMARC fully implemented on your domain is one of the best ways to protect your brand from impersonation.
Brand Indicators for Message Identification (BIMI): Provides domains that already use DMARC for authentication an extra layer of protection by displaying their brand logo in email messages. This helps recipients visually identify when an email is legitimate, and helps companies build additional brand awareness through email campaigns.
The Advanced Fortra Advantage
Agari DMARC Protection uses SMTPS, as well as DMARC, to encrypt email messages and prevent attacks from spoofed domains. In addition, TLS and DMARC prevent inboxes from receiving fake emails from companies who have had their email spoofed.
Phishing attacks that use lookalike domains trick unsuspecting recipients into clicking links or sending sensitive information by pretending to be a trusted sender. These attacks can occur directly over a SMTPS connection since they don’t need to abuse a lack of encryption in order to succeed.
By combining SMTPS with Agari DMARC Protection, organizations can deploy an email security strategy that stops email-based attacks on all levels. For email protection that goes beyond SMTPS, see how Cloud Email Protection works in action, or schedule a demo to learn more.
