In the FBI's latest IC3 report, advanced attacks like spear phishing, spoofing, and BEC had nearly 320,000 complaints reported in 2023 – resulting in total losses in excess of $4.6B!
Augment Your Enterprise's Email Architecture with Fortra's Cloud Email Protection
It’s no secret that threat actors rely heavily on impersonation and social engineering to slip malicious emails past defenses and into user inboxes. And the reality is that Secure Email Gateways struggle to detect advanced threats, such as Business Email Compromise and spear phishing attacks.
According to recent statistics reported by Fortra experts, more than 98% of threats that bypass traditional email security defenses rely on impersonation and social engineering. To make matters worse, these tools have been slow to adapt to cloud-based architectures, forcing enterprises that migrate to cloud email to become susceptible to cloud phishing and compromise their security.
Enterprises need robust email security that both stops advanced threats in their tracks and integrates seamlessly into cloud-based environments.
Move from Email Threat Protection that Suffices to the Most Advanced ICES
(Integrated Cloud-Based Email Security) Solution
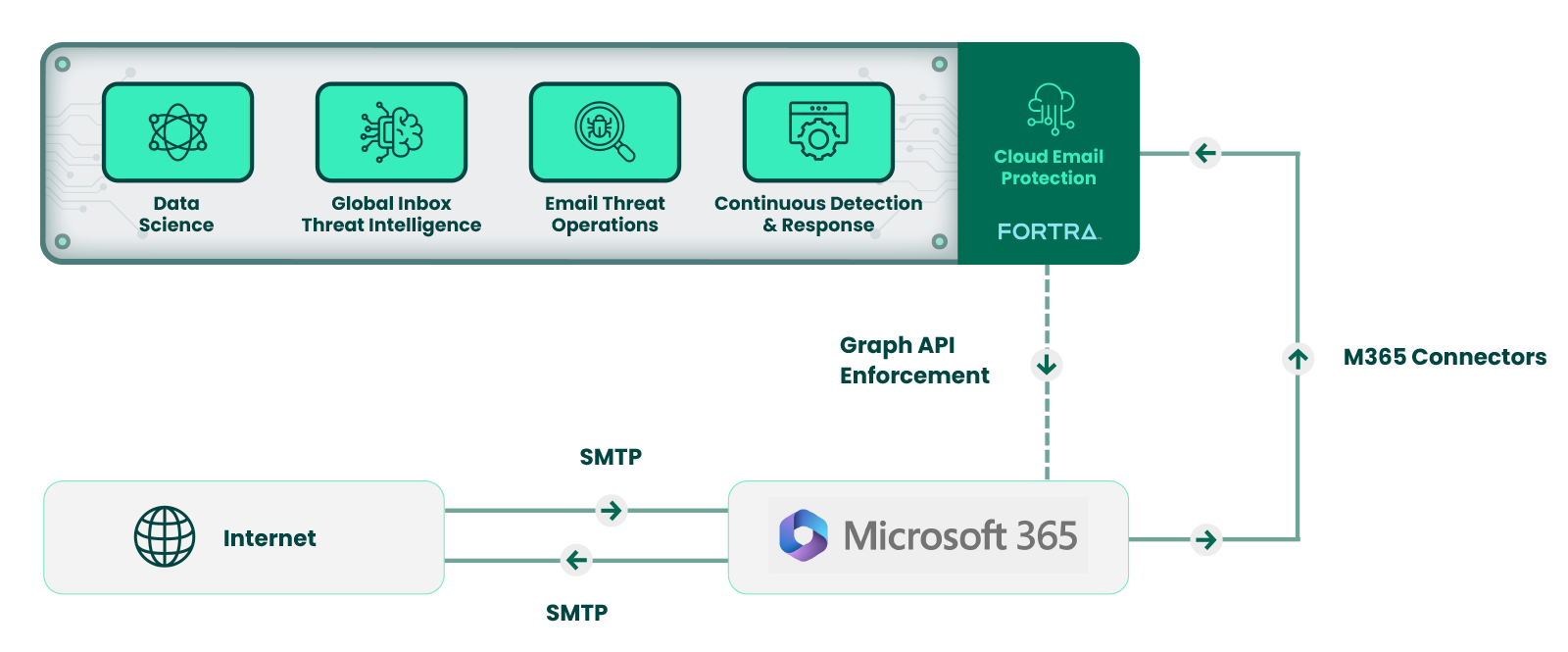
Fortra’s Cloud Email Protection is a cloud-native platform that uses AI-powered data science, global threat intel, and automated threat remediation to keep user inboxes free from advanced email threats like cloud phishing, and API-enabled to seamlessly deliver threat protection in various email environments.
Cloud Email Solution Features
Global industry leaders count on Fortra to avoid the cost and business disruption that comes from rapidly evolving email tactics, such as impersonation.
Advanced Data Science
The data science behind Cloud Email Protection is an advanced system of machine learning (ML) models, Large Language Models (LLMs), and neural networks that work together to accurately detect impersonation and social engineering techniques used in messages.
Fortra's team of expert data scientists and email threat researchers have extensive experience in practical applications of modern ML and AI technologies and ensure that the platform is trained and optimized to detect unknown threats that bypass traditional email security controls.
Global Inbox Threat Intelligence
Fortra's Cloud Email Protection platform comes with integrated feeds from Fortra’s Global Inbox Threat Intel. Every day, Cloud Email Protection ingests hundreds of curated, high-fidelity threat indicators from newly observed threats that have bypassed traditional Secure Email Gateways.
All while it continuously scans email traffic and inboxes for these indicators, detecting and removing them automatically.
Email Threat Operations
In addition to advanced data science and global inbox threat intelligence, Cloud Email Protection benefits from a team of expert analysts that dig deep into threat data across its customer base to proactively hunt for novel attacks.
This team leverages current events, advanced techniques like pivoting, and customer performance insights to operationally detect advanced email threats. Additionally, input from this team is constantly being fed into our global threat intelligence feed and data science models to further enrich the platform.
Automated Remediation
Cloud Email Protection features a robust logic-based policy configuration and enforcement engine called Continuous Detection and Response (CDR). CDR uses Fortra's Advanced Data Science, Global Inbox Threat Intel, Email Threat Operations, as well as customer-specific policies to automatically purge threats across all inboxes.
Customers can use Continuous Detection and Response to tailor policies to their email environment, remove/quarantine messages, send alerts, and trigger third-party orchestration tools.
API-Based Integration
Email environments are notoriously complicated. Most organizations need constant access to email and work to eliminate any single point of failure.
Cloud Email Protection is a cloud-native platform that uses an API integration to quickly deploy alongside Microsoft 365, Exchange, and Google Workspace environments – whether on-premise or hybrid – to protect enterprises from phishing attacks.
To learn about Fortra's Advanced Data Science and more, read our whitepaper.
How Fortra's Cloud Email Protection Platform Melds It All Together
Our CFO's likeness was used to falsely convince our AP to wire funds offshore. Fortunately, Fortra’s Cloud Email Protection detected and stopped the threat before damage occurred. The peace of mind that Fortra provides us empowers us to go about our day knowing we are protected, even from social engineering attacks that are hard to detect.
Emmanuel Appiah, Sr InfoSec Analyst, Apria Healthcare Group
Complementary Fortra Solutions
Fortra's Cloud Email Protection pairs well with the following Advanced Email Security & Digital Risk Protection solutions:
Suspicious Email Analysis
Service that expertly triages and responds automatically to user-reported emails
Service that expertly triages and responds automatically to user-reported emails
DMARC Protection
Solution that automates and simplifies DMARC email authentication and SPF & DKIM protocols
Learn More
Solution that automates and simplifies DMARC email authentication and SPF & DKIM protocols
Domain Monitoring
Service that streamlines mitigation through registrar partners and escalation procedures
Learn More
Service that streamlines mitigation through registrar partners and escalation procedures
Security Awareness Training
Interactive modules and courses that train employees to identify cyber threats
Learn More
Interactive modules and courses that train employees to identify cyber threats
Threat Intel Services
Service that equips SOC teams with insights that aid in threat disruption and enrich controls
Learn More
Service that equips SOC teams with insights that aid in threat disruption and enrich controls
